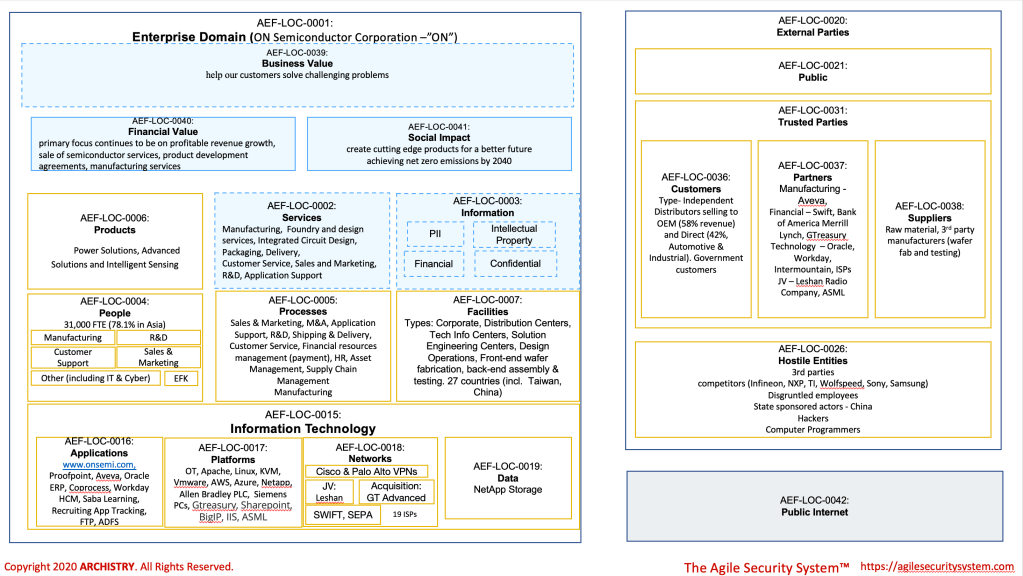
Delve into another instance of harnessing the Agile Security System. This time the focus is on ON Semiconductor. For insights into the methodology, kindly consult the Rogers post. This article will spotlight a couple of ways in which this approach can prove beneficial for individuals in these specific functions:
- Security Operations Center (including cloud)
- Incident Response
- Security Technology Management (i.e. firewall, email, EDR, cloud-native tools etc.)
- Identity Access & Management
- Identity Operations
- Threat hunting & Intelligence
- End point management.
- Forensics
- Detection Engineering
- Data Protection Engineering
- Vulnerability Management
Value of Agile Security System “Artifacts” for Non-Architecture Functions
- It addresses the fundamental “why” behind your role, serving as a source of inspiration. If you haven’t already, consider watching Simon Sinek’s older, but insightful video on this topic (https://youtu.be/Jeg3lIK8lro?si=K9xJGldk1AfQ-zMT) or read his book, “Start with Why.” Utilizing the business contextual architecture enables you to connect your role with the organization’s value. This approach reminds you that your role is an integral part of a larger system or context. Despite the allure and “coolness” of your role (e.g., Penetration Tester, Digital Forensic Examiner, Cloud Security Architect, or Threat Intelligence Analyst), cybersecurity doesn’t operate in isolation; it exists to deliver value. In your role, you contribute to the organization’s success by providing value that aligns with its goals. To put it another way, your role exists to the help the company “win” by helping them managing risk, so they “score points,” “win the game,” “win the championship or season” and be “winners” over decades of time (e.g. IBM, AT&T, GE etc.) What happens to players that don’t help their teams’ win? Yep, they get traded (here is video by Reed Hasting that talks about this analogy).
Side note – I also like Sinek’s view on high performing teams too (https://www.youtube.com/watch?v=zP9jpxitfb4 and https://www.youtube.com/watch?v=PTo9e3ILmms)
At ON, you create value by assisting customers in solving complex problems, contributing to the development of cutting-edge products, supporting the achievement of net-zero emissions by 2040, and facilitating profitable revenue growth. You must help ON do this better and before their competitors. That is it .
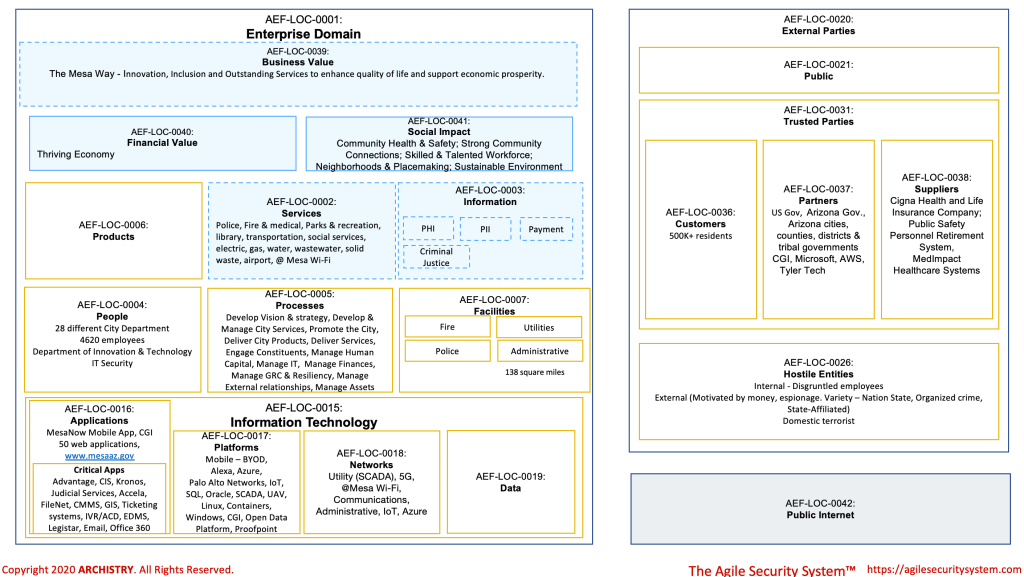
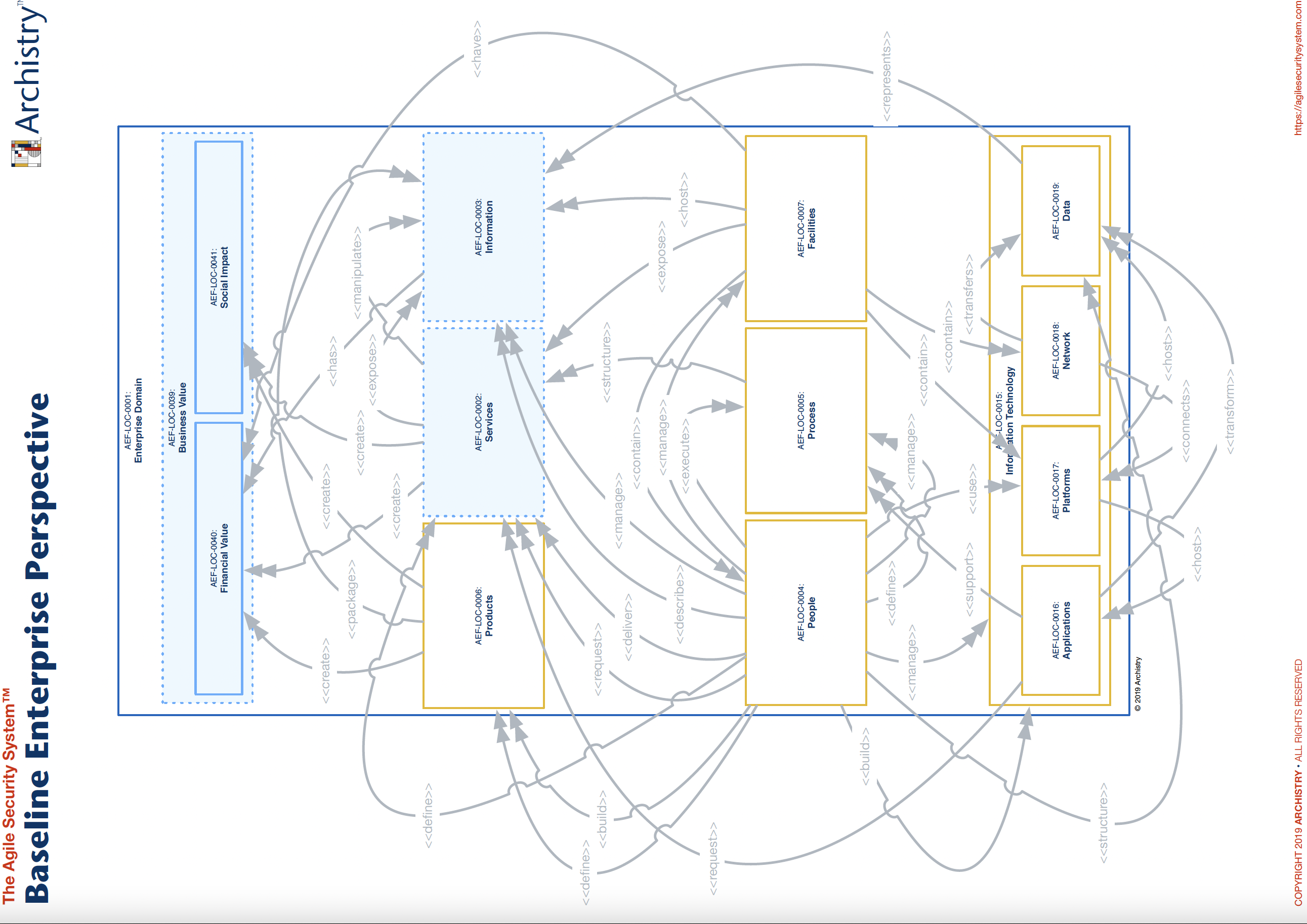
This linkage between your cybersecurity function and value becomes clearer when using the Agile Security System’s Baseline Enterprise Perspective ( Figure 2) and the company specific business architecture. The Baseline Enterprise Perspective shows the relationships between the different domains. For example, the “Other” (Figure 1) in the People domain help <<deliver>> services that <<create>> financial, social and business value. Another example is how the “Other” (Figure 1) in the People domain <<manage>> and <<build>> Information Technology, which, in turn, <<supports>> Process and <<represents” Information, which in turn, <<has>> financial value.
It aids in prioritizing operational activities of your cybersecurity functioning by providing answers to key questions such as:
- Where should I begin vulnerability scanning or requiring continuous scanning?
- What area needs to be “hunted” (and cleared of) for threat actors?
- What alerts and incidents should the SOC and/or IR team prioritize?
- Where should data protection engineering begin focusing their efforts?
- What changes should be assigned a higher risk within the change management process?
- What roles should undergo IAM access reviews?
- What detection alerts should be created by the Detection Engineering team?
- What use cases should the forensics team plan for?
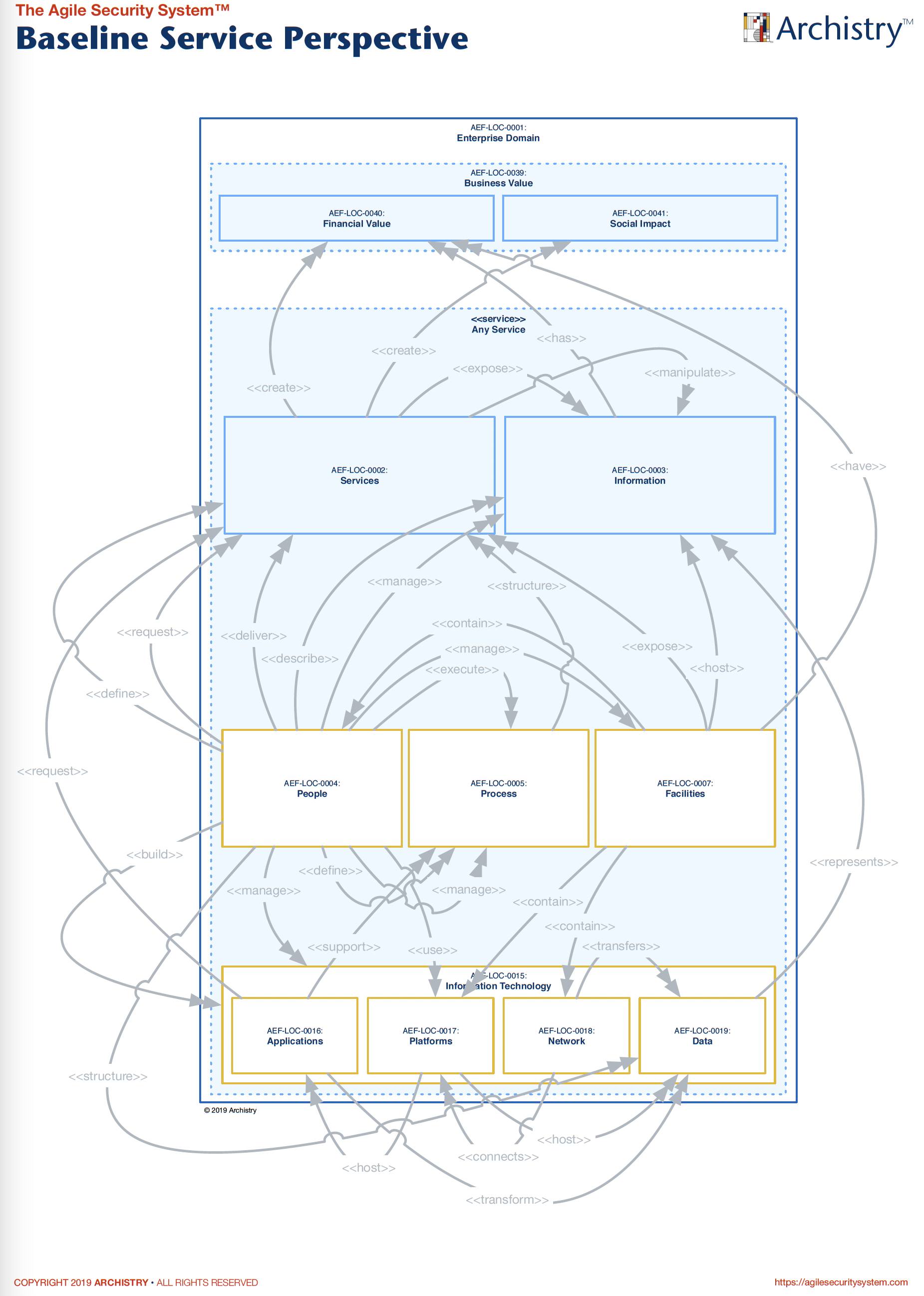
The answer to questions like those above can be uncovered using the architecture depicted in Figure 1 as well as creating an Agile Security System Baseline Service perspective for each service listed in the Services domain (see Figure 3 for the Baseline Service perspective). While the architecture may lack specific technical details like hostnames and IP addresses, obtaining this information and ensuring its accurate linkage to the appropriate parent domain is easily achievable. The primary takeaway is that you now possess an understanding of the crucial services, products, and information contributing to value creation. Our mission is to safeguard and enable this value.
In the case of ON, it’s imperative to conduct vulnerability scans and complete IAM access reviews for applications, platforms, and networks supporting identified in the processes. With the recent acquisitions of “EFK” and “GT Advanced,” can a Zero Trust Network Access solution be deployed to expedite integration while minimizing risks? Does the threat hunting team thoroughly assess the networks associated with EFK and GT Advanced? Do they replicate this exercise when a manufacturing facility expands operations or a new one is built? Did the threat intel team and 3rd party risk team participate in the due diligence process for acquiring EFK and GT Advanced as well as the joint venture with Leshan?
Furthermore, have the detection engineering, data protection engineer, and SOC teams prioritized alerts, DLP rules, and responses for unlikely or unauthorized scenarios? For instance, if an employee in the Sales, Marketing, or IT teams transfers IP information from the US to a Chinese location, how are these situations managed? When the engineering team overseeing firewalls upgrades a firewall responsible for routing/monitoring traffic from a manufacturing process, should this change be considered high-risk even with a high-availability setup? Considering scenarios where an IR or forensic team might need to take a system offline, how do they assess the potential impact of such a decision? IR and forensics teams can refer to the business contextual architecture for insights!
Do you have the responsibility of devising tabletop exercise scenarios? It’s no surprise that you can utilize the business contextual architecture to aid in this task. For example, Understanding that Sales & Marketing services and associated processes play a crucial role in ON’s success, you could focus a tabletop exercise focused on the systems supporting Sales and Marketing processes and what happens if there are unavailable due to a ransomware attack.
Initial Observations
- ON must protect their intellectual property (IP). In the same aforementioned article by Anne Meixner, it is highlighted that individuals with access to critical systems and data within a company can become a security risk, either through intentional malicious actions or unintentional compromise due to human error. An illustrative instance of human error is provided, where engineers inadvertently leaked Samsung trade secrets using ChatGPT. To mitigate such risks, implementing administrative controls such as non-disclosure agreements, confidentiality agreements, trademarks, and educational initiatives becomes crucial. This underscores the need for a well-established insider risk management program to address and mitigate potential threats originating from within the organization. Effectively safeguarding ON’s IP necessitates the integration of security objectives that prioritize Confidentiality, Classification, Threat-Managed, Access-Control, Education, Authorization, Identification Legal, Duty-Segregation, Governance, Risk-Management and Monitoring.
- It is imperative for ON to possess advanced capabilities in intrusion detection, web security, threat intelligence, and training. According to the 2023 Verizon data breach report, surprisingly, only 1% of reported breaches in the Manufacturing sector involved partners, while a significant 90% were attributed to external threat actors. The predominant attack patterns observed were system intrusions, social engineering, and basic web attacks. In the context of motivation, threat actors primarily targeted organizations in the Manufacturing sector for financial gain, espionage, and convenience. Given this landscape, robust threat intelligence capabilities play a pivotal role in comprehending, identifying, and containing attacks driven by espionage motives.The above requires the cybersecurity strategy to incorporate the security objectives that prioritize Confidentiality, , Threat-Managed, Access-Control, Education, Risk-Management and Monitoring.
- A comprehensive vulnerability management program is crucial for ON’s security. Once again, in the article “Securing Chip Manufacturing Against Growing Cyber Threats,” Meixner references Joon Ahn, a vice president in the IT division at Amkor Technology, a company specializing in wafer level and packing assembly. According to Ahn, a notable gap in the semiconductor industry lies in connectivity vulnerabilities. Smart manufacturing technologies heavily rely on connectivity, introducing vulnerabilities as hackers target unsecured network connections to gain access to sensitive systems. The vulnerability management program should be leveraging CVSS 4.0 and have adequate resources assigned to monitor potential vulnerabilities affecting ON’s environment. To address integrity-related security objectives, ON must prioritize Vulnerability-Managed, Change-Managed, Configuration-Managed, Auditable, and Maintenance as essential components of its security strategy.
- As an “outsider” of the semiconductor industry, a semiconductor company like ON has to invest A LOT of capital and operational funds to setup a manufacturer facility. One University of Berkeley study has an estimated range of 3-4 billion US dollars. Every dollar spent on cybersecurity is a dollar taken away from running a manufacturer facility or profit creating service or process. To state the obvious, any security strategy needs to incorporate the security objectives of Cost-Effective and Efficient.
- It seems that ON acknowledges the necessity of incorporating education and awareness into their cybersecurity strategy for both customers and suppliers (see https://www.onsemi.com/company/events/webinars/don-t-let-cybersecurity-become-the-weakest-link-in-the-automotive-system for an example).
- Security, encompassing both facility and infrastructure, including cybersecurity, is crucial for ensuring safety, operational effectiveness and profitability. As articulated in ON’s 10K filing, any inability to use manufacturing facilities, testing facilities, and external manufacturers at anticipated or minimum purchase obligation levels, or a scenario where production capacity expands without a proportional increase in revenue, may lead to fixed costs and operating expenses associated with these facilities and arrangements not being fully absorbed. This could result in elevated average unit costs and diminished gross profits, potentially causing a significant adverse impact on ON’s operational outcomes. Additionally, as Joon Ahn, vice present at Amkor Technology summarized in an article on semiengineering.com, physical security becomes increasingly important as manufacturing facilities become more automated. Unauthorized access to the factory floor can result in equipment damage or theft. Any security strategy needs to incorporate the security objectives of Risk-Managed, Threat-Managed, Access-Controlled, and Interoperable.
- Application security is fundamental. This becomes even more clear and scarier when you read the opinion post by Lumpkin and Levin (2022) in the article “The mother of all ‘zero-days’ – immortal flaws in semiconductor chips.” They state the following:
Every chip starts life as a software program before it is fabricated, mostly in Asia, and mostly in Taiwan, into a chip. The process that transforms design code into “sand in the hand” silicon is just as vulnerable today as consumer applications were in the early 2010s, and for all the same reasons. The impact is deeper and more penetrating because once a chip is compromised, it is nearly impossible to patch. It might be in space or under an ocean. Our enemies know this too.
This means that software flaws needed to be detected and remediated continuously throughout the development lifecycle and iterations. Application security cannot be bolted on, but designed and built in. Any ON cybersecurity strategy must be structured to address the security objectives of Risk-Managed, Awareness, Threat-Managed, Integrity-Assured and Compliant. - Like all organizations, ON must gather and keep up with laws and regulations and translating them into physical, administrative and technical controls. As a manufacturer, ON has several of same sources for requirements as those posted for Rogers. Cybersecurity strategy must be organized to address the security objectives of Auditable, Legal and Compliant. Here are some potential sources for cybersecurity requirements: a) United States Patent and Trademark Office; b) United States Uniform Trade Secrets Act; c) United States Sarbanes-Oxley Act of 2002; d) European Union’s General Data Protection Regulation; e) United States Patent and Trademark Office; f) Canadian Bill C-27; g) SEMI E187 and SEMI E188 Standards; h) Creating Helpful Incentives to Produce Semiconductors and Science Act; i) United States Inflation Reduction Act; j)the International Traffic in Arms Regulation promulgated under the Arms Export Control Act (“ITAR”; k) United States Foreign Corrupt Practices Act (“FCPA”); l) anti-boycott provisions of the U.S. Export Administration Act; m) United States Responsible Business Alliance (“RBA”) Code of Conduct United States; n) FCPA (anti-corruption laws); o) NIST 800-171.
If you’re curious about how the Agile Security System manages requirements engineering, please consult the Figures 5, 6, and 7 provided below (prior to the questions section). It’s important to note that these figures are not complete and would require further iterations. The figure also only show the first page of the domain analysis worksheet too. This aspect is notably robust within the Agile Security System, allowing you to follow a set of requirements, objectives, or goals within a specific domain, along with their associated risks and mitigations. Notably, these aspects directly correspond to cybersecurity strategy. This process can be defined as the threat modeling of the business context. As per the threat modeling manifesto, the process involves addressing four key questions: a) What are we building (requirements, goals, objectives)?; b) What could go wrong (risks)? c) How do we plan to address it (mitigations)? d) Have we done an adequate job? The final question involves a “gut check” to evaluate the documentation. Ideally, all questions are collaboratively answered by the team, avoiding dependence on a singular “hero threat modeler.” - Establishing an Enterprise Architecture (EA) capability is imperative to provide a systematic approach to processes and architecture. This is essential for supporting the design and implementation of a new manufacturing facility and the integration of new companies. The EA capability should also encompass cybersecurity architecture.
As noted in ON’s 10K filing from 2022, if ON is
unable to successfully integrate new strategic acquisitions, which could materially adversely affect our business, results of operations and financial condition. Per Successful acquisitions and alliances in our industry require, among other things, efficient integration and aligning of product offerings and manufacturing operations and coordination of sales and marketing and research and development efforts, often in markets or regions in which we have less experience. Risks related to successful integration of an acquisition include, but are not limited to: (1) the ability to integrate information technology and other systems; (2) issues not discovered in our due diligence
ON’s cybersecurity strategy must incorporate the security objectives of Risk-Managed, Threat-Managed, Integrity-Assured, Governed, Efficient , Cost-Effective, Monitored, Usable and Adaptable. - For a global company, effective cybersecurity capabilities must encompass attack surface management and threat intelligence. ON seems to operate with 19 Internet Service Providers (ISPs) and 102 visible endpoints on the internet (including 4 DNS servers and 4 email servers via Proofpoint). It is crucial to vigilantly monitor the contraction and expansion of this attack surface to identify potential weaknesses, such as configuration errors or systems without system owners
- Like Rogers Corporation and the City of Mesa, ON has a cloud presence (in AWS). It appears that may be migrating their website, www.onsemi.com to AWS (beta-www.onsemi.com). I have the same observations for ON as those for Rogers Corporation.
- ON must retain highly skilled personnel, and its cybersecurity program should not be overly burdensome to the extent that employees choose to leave the company. It is crucial that the cybersecurity program at ON is competitive, efficient, effective, and user-friendly to avoid making it overly burdensome and cumbersome.
- ON provides products to companies in the industrial sector, contributing to the development of more intelligent cities, factories, and buildings. The demand for cybersecurity in product delivery is expected to rise as ON’s “smart” technologies continue to expand, and the company adopts its own technology in its manufacturing facilities. Another term used to describe a more intelligent factory is Industry 4.0 (or the 4th Industrial Revolution), as per ChatGPT 3.5, involving the integration of digital technologies, the Internet of Things, artificial intelligence, and data analytics into the industrial process. Clearly, as manufacturing processes become more digitized and interconnected for ON and its customers and suppliers, solving cybersecurity challenges becomes crucial.
- Managing Third-Party/Supply Chain Risks is crucial. This involves overseeing aspects such as monitoring, access control, incident response, and governance. However, it’s crucial to strike a balance; third-party risk management practices and processes must not become so burdensome that companies are disinclined to engage in business collaborations. The reliance of manufacturing and operations on third-party facilities, suppliers of raw materials, and software is significant. Identifying alternative manufacturers and suppliers can be a time-consuming and expensive endeavor, often complicated by a limited pool of qualified providers. Collaboration and a well-practiced incident response plan are vital when dealing with connections to third parties. It’s essential to limit exposure and prioritize containment. This means restricting third-party access to a specific set of resources, thereby minimizing the potential impact. Regular validation of access, following a zero-trust approach, adds an extra layer of security and assurance.
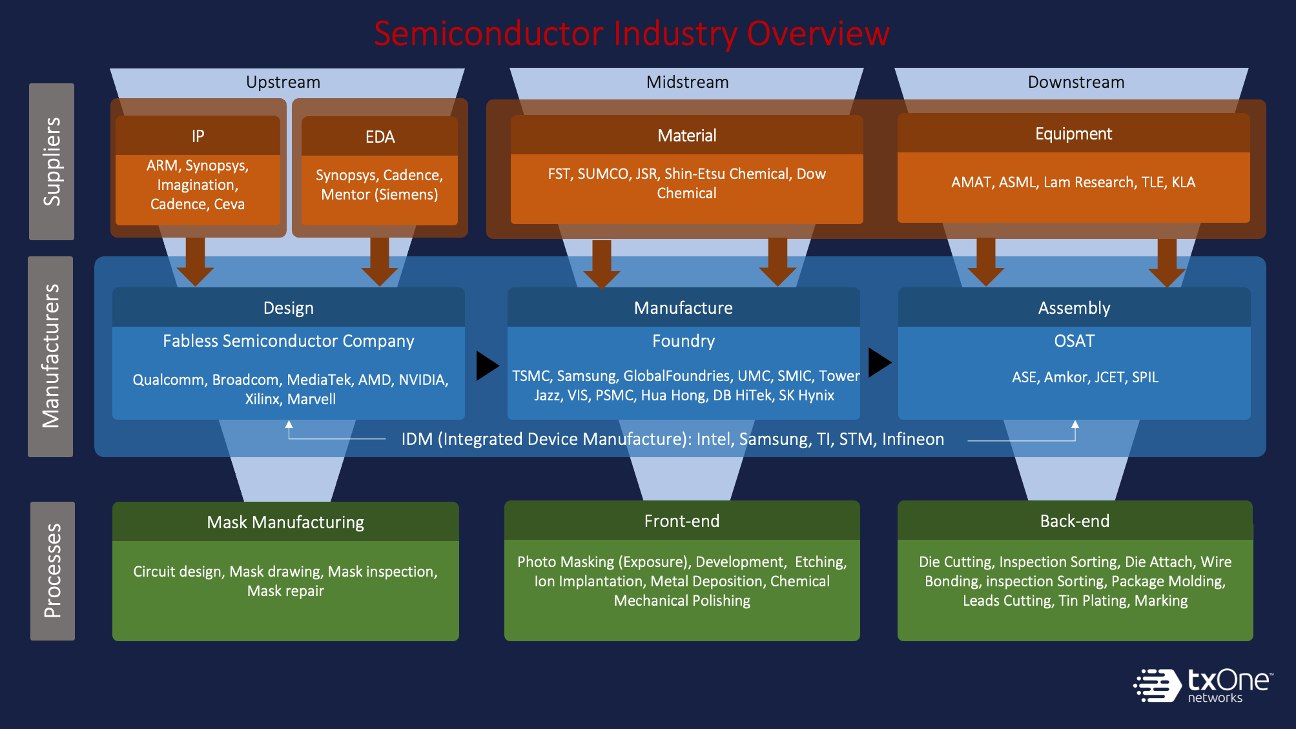
The article, “Securing Chip Manufacturing Against Growing Cyber Threats” by Anne Meixner states that 60% to 90%, of impactful security issues stem from suppliers. This is, in part, due to a growing level of interdependency among companies in this industry, and ON is likely no exception. As the Meixner’s article summarizes the current situation of 3rd party interdependency.
Where methodologies and standards do exist for security, they often are confusing, cumbersome, and incomplete. There are plenty of gaps, particularly among some of the smaller suppliers of IP, equipment, and materials, where security remains primitive at best. This is partly due to the fact that in the past, much of the focus was on vulnerabilities in chips and chipmakers. But there is an increasingly high level of interdependency between companies in the semiconductor industry. The number of interactions is growing as complexity increases, and as chip designs become increasingly heterogeneous.
Figure 4 provides a conceptual view of the interdependency the semiconductor industry Change Managed, Monitored, Risk-Managed, Access-Controlled, Threat-Monitored, Threat Management, Governed, and Vetted are key attributes that need to be part of any cybersecurity strategy.

Initial Questions
- Is the accuracy of the business architecture confirmed, and are there any essential elements missing?
- Does a reference architecture exist for a specific manufacturing facilities that includes cybersecurity requirements? That is, business knows the cost associated with the cybersecurity infrastructure and tools for a facility. Has IT provided a BOM for the different facility types? Does cybersecurity have a process to on-board a facility into their processes?
- How are risk management and policy governance handled? Is ON the culture open an approach similar to one discussed for the City of Mesa?
- How is the integration handled in the event of a merger with a new company?
- What is the logistics process for transporting products between facilities? For instance, how are silicon wafers manufactured in the Czech Republic transported to a facility in another company? How are these protected?
- What role does IT and Cybersecurity play in the expansion or installation of a new manufacturing facility?
- In what ways can Cybersecurity support and safeguard Research and Development (R&D) efforts?
- The prevalence of VPN connections is notable. With 23 internet-accessible VPN endpoints (23 out of 103, or 22%), what is the reason for this high number?
- Is there an ongoing project to transition http://www.onsemi.com to AWS (beta-www.onsemi.com, 23.22.192.64)? Has AWS been design with their cloud adoption framework? Does the SOC use cloud native tools or 3rd party tools for security cloud operations?
- Is there representation from ON at Semicon West, and is Semicon West considered a reputable conference?
- Is there a defined policy or stance regarding Generative AI, and does ON have an Emerging Technology Committee in place?
- Is ON following the guidance from the NSA? Is it applicable?