www.linkedin.com/pulse/ecsas-reference-architecture-practice-neil-rerup-yoiyc
Tag Archives: architecture
What is reference architecture?
https://hjortberg.substack.com/p/reference-architecture-explained
Great quote from post above by @
great reference architecture doesn’t limit possibilities, it expands them by providing a strong foundation for innovation.
A reference architecture is a recommendation, not a law. It is a flexible, high-level framework that provides guidance and best practices for designing systems in a specific domain. It is not mandatory, not a specific implementation, and not a one-size-fits-all solution. Instead, it serves as a reference point that you can adapt to your unique needs and context.
What does Lego have to do with Cybersecurity Architecture?
Great question! Despite the risk of spoiling future “ice breakers,” let me share an exercise that answers the question through action. Enough talking—no academic architects needed today!
- Purchase 3-4 identical LEGO kits, each containing between 100-200 pieces. Choose a set that aligns with your organization’s field. For instance, if you’re in healthcare or manufacturing, opt for a car model.
- Unbox all the kits, combine all the pieces into a single bag, mix them thoroughly, and then pour them into a pile.

3) Show a “rules” slide. Below is an example from the last exercise.

4) organize the participants into group of 2-3 people
5) tell people to start.
So, what typically happens next? Well, people love building with LEGO bricks—who doesn’t, right? In every instance I’ve run this exercise, everyone immediately starts grabbing pieces and building something. Why do they do this? Maybe they’re eager to relive fond childhood memories. Perhaps they’re doers who just want to complete the task. Or maybe they feel the competitive pressure of the timer. Regardless, the architects communicate with each other and have a great time. While no one has burst into singing “Everything is Awesome” (see this https://youtu.be/9cQgQIMlwWw?si=ODUGkwCohYu8eeuK), I usually walk around, taking pictures to capture their progress and final creations.




Now, you might be curious about how I handle questions. For this exercise, I used Microsoft Copilot to create a fictional press release between onsemi and Waymo. Depending on the question, I would share this press release.. I have highlighted some key “attributes” within the press release. If you noticed the quotes around “attributes,” you’re right—they refer to SABSA business attributes.
Fictional Press release by Microsoft Co-pilot–
Press Release
onsemi and Waymo Announce Strategic Partnership to Develop Solar-Powered Autonomous Vehicles with Open Design Access
Phoenix, AZ – September 21, 2024 – onsemi (Nasdaq: ON), a leader in intelligent power and sensing technologies, today announced a strategic partnership with Waymo, an autonomous driving technology company, to develop a new generation of solar-powered autonomous, 1 person automobile. This collaboration aims to integrate onsemi’s advanced semiconductor solutions with Waymo’s state-of-the-art autonomous driving systems to create a sustainable and efficient transportation solution. Additionally, the partnership will make the vehicle design available to the public, encouraging innovation and collaboration within the industry.
Hassane El-Khoury, CEO of onsemi, stated:
“We are thrilled to partner with Waymo on this groundbreaking project. This partnership not only represents a significant advancement in sustainable and autonomous transportation but also embodies our commitment to open innovation. By making the design of our solar-powered vehicle available to the public, we aim to foster a collaborative environment where innovators and enthusiasts can contribute to the future of mobility.”
Key Requirements of the Partnership:
- Integration of Solar Technology: The vehicles will be equipped with advanced solar panels to harness renewable energy, significantly reducing the reliance on traditional fuel sources.
- Advanced Semiconductor Solutions: onsemi will provide high-efficiency power management and sensing technologies to optimize the vehicle’s performance and energy consumption.
- Autonomous Driving Systems: Waymo will integrate its latest autonomous driving technology to ensure safe and reliable operation of the vehicles.
- Sustainability Goals: Both companies are committed to achieving significant reductions in carbon emissions and promoting the use of renewable energy in the automotive sector.
- Open Design Access: The partnership will release the vehicle design to the public, allowing engineers, developers, and hobbyists to access and contribute to the development of solar-powered autonomous vehicles.
Innovation and Development: The partnership will focus on continuous innovation and development to push the boundaries of what is possible in autonomous and sustainable transportation.
About onsemi: onsemi (Nasdaq: ON) is driving disruptive innovations to help build a better future. With a focus on automotive and industrial end-markets, the company is accelerating change in megatrends such as vehicle electrification and safety, sustainable energy grids, industrial automation, and 5G and cloud infrastructure. onsemi is headquartered in Phoenix, Arizona, and has a global network of manufacturing facilities, sales offices, and design centers.
About Waymo: Waymo is an autonomous driving technology company with a mission to make it safe and easy for people and things to move around. Since its inception as the Google Self-Driving Car Project in 2009, Waymo has been focused on building the world’s most experienced driver and making it available to everyone.
————————————————————————————————
In this particular exercise, I would have provided the instructions that come with the LEGO set if participants had asked to see the published “open design.”
After the time has elapsed, I ask the following question:
- What does LEGO have to do with cybersecurity architecture?
Here are some answers:
- Efficient, reusable building blocks
- Modularity of the blocks
- Scalability of the blocks.
- Interconnected nature of blocks allow adaptable and efficient models
All of these answers are accurate. However, the key answer is requirements gathering. How do you know what your customer wants, in this case, the CEO of onsemi, if you don’t ask them? If participants had asked “great questions,” as Andrew Townley always advocates, I would have given them pieces of paper with attributes important to Hassane in this fictional scenario.

Of course, you can potentially guess some of the things the customer wants. For example, in this instance, each team created a solar-powered car and a one-person car. You can see the check marks beside the attributes in the picture. However, the teams missed the business objectives of the Waymo partnership: safety and autonomy. How does the final product compare to the imaginary one that Hassan had in mind?

What does this mean? We should always help our customers deliver value. We cannot be roadblocks, even ones made of LEGO bricks. We must always prioritize safety. One way to keep them safe is by ensuring we ask and understand their requirements. This increases the likelihood that the operationalized solution meets the needs of the organization. Don’t get too caught up in the pressure of a “timer.” Don’t get me wrong. We got to deliver and timelines need to be met. Pause, do your homework, ask great questions, and get those requirements documented.
Business Contextual Architecture – Public Sector Case Study
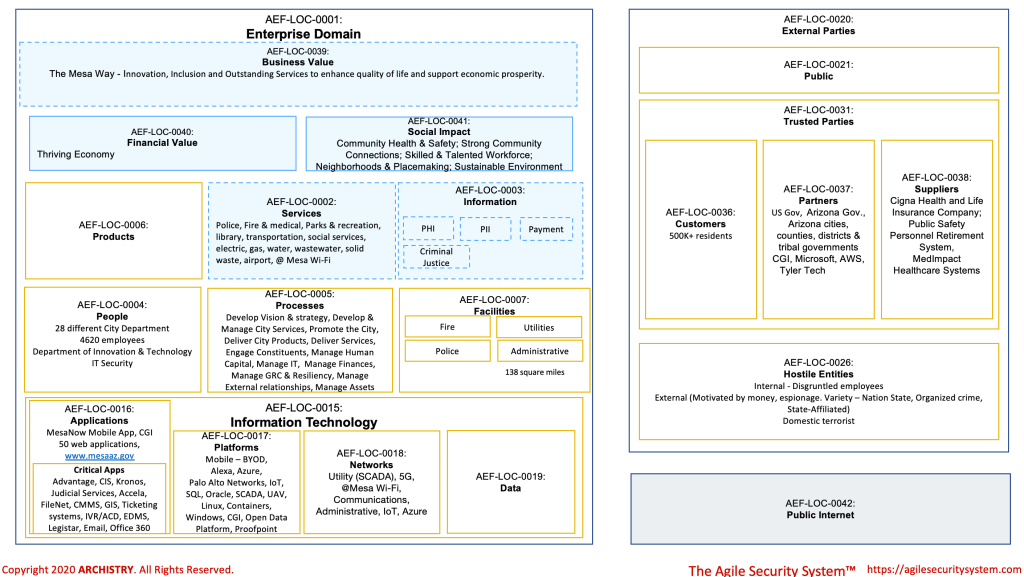
Presented here is another segment in the series focusing on constructing a business contextual architecture, utilizing the Agile Security System devised by Andrew Townley. This particular case study centers on the public sector, specifically examining the context of the City of Mesa, Arizona. The figure below is the Domain Impact Worksheet from the Agile Security System.
Methodology
Please note that I use the phrases of “security objectives” or “business objectives” throughout the observations below. This is an architectural or strategy technique that I learned from SABSA and Andrew Townley. SABSA refers to them as “business attributes.” Business attributes are abstractions of risk mitigation strategies or enablement strategies that must be met for an organization to deliver or achieve a desired outcome, goal or objective. The specific security objectives, like Available, Risk-Managed, and associated definitions are from “Getting Started with the Agile Security System” (Townley, 2023, Appendices E and F). A cybersecurity strategy and operations need to incorporate and deliver on these cybersecurity objectives.
Observations
- The official website, www.mesaaz.gov, stands as the primary brand for the City. Residents depend on the site’s continuous availability, anticipating unfettered access at all times. Moreover, residents expect that any information gathered from them is handled with the utmost protection. The security objectives, encompassing Availability, Governed, Duty-Segregated, Reputable, and Safe, are paramount in this context. Additionally, Customer-focused, Usable, and Resourced are other important business objectives.
- Data.mesaaz.gov and openbudget.mesaaz.gov assume a pivotal role in promoting the City’s strategic priority of cultivating “Strong Community Connections.” The essence of their importance is rooted in harnessing data analytics, minimizing disruptions to stakeholders, and aligning with the objective of ensuring transparency with citizens, thereby helping the implementation of a smarter Mesa. These two websites share the same security objectives as www.mesaaz.gov, including Availability, Governed, Duty-Segregated, Reputable, and Safe. Additionally, an overarching objective for Data.mesaaz.gov and openbudget.mesaaz.gov is to be Interoperable.
- Complexity and diversity of City Services are unapparelled. The City of Mesa operates utilities, medical service, police, transportation, library, parks, social services and public Wi-Fi. These services are delivered by people operating in 28 diverse departments within the City of Mesa. The services are structured by unique and overlapping processes and expose different types of information to customers and employees. The intricate complexity and diversity of services provided by the City of Mesa give rise to distinct business requirements, legislative demands, and a varied landscape of attack surfaces that require targeted risk mitigation strategies. A notable example is the existence of 52 internet-accessible web applications supporting diverse city processes. Consequently, it is imperative to incorporate critical security objectives into the cybersecurity strategy to effectively address these challenges. The essential security objectives include Risk-managed, Compliant, Documented, Recoverable, Access Controlled, Compliant, Integrity-Assured.
- Given the complexity and diversity of the City of Mesa’s services, the maturing of an Enterprise Architecture (EA) capability becomes imperative. The City has recognized the importance of maturing such capability by incorporating it into their IT Strategic Plan and Roadmap document. EA capability needs to incorporate and be integrated with Cybersecurity Architecture and Solution Architecture These architecture domains play a crucial role in ensuring that solutions are not only technologically sound but also aligned with key cybersecurity objectives and requirements. Customer-Focused and Governed are key business objectives. Enterprise Architecture can help break down silos, down silos, explore new technologies / capabilities, ensure IT alignment with the 50 year plan (see https://plan.konveio.com/tomorrows-mesa-2050-general-plan), and IT governance.
- Effective risk management and policy governance are indispensable for municipalities like the City of Mesa, particularly in the context of limited funding for cybersecurity compared to federal governments or private corporations. Prioritizing IT security and privacy funding via risk management is paramount. A key facet of risk management involves identifying the appropriate owner / role, whether it be a City Manager, Mayor, or Department Head, to accept, mitigate, or transfer risks. The integration of risk management with a comprehensive City-wide framework, beyond cybersecurity and privacy, is essential. The adoption of a “Domain Framework” based on SABSA becomes instrumental, where each domain is owned by an accountable individual responsible for setting policies and risk appetite, while adhering to the parent risk parameters and policies. For example, the City of Mesa via the Mayor and City Council would set a city wide risk appetite level and general cybersecurity risk policy (i.e., Enterprise Domain). All child domains (e.g. Process, Information, Information Technology) would have to adhere to the risk appetite and policies of the parent (i.e., Enterprise Domain). This approach enables the appropriate role to make and own risk decisions similar to the ones they are already making in finance, legal, and HR. Cybersecurity would need to be consulted on cybersecurity policy and risk decisions. This approach also removes IT Security as the perceived owner of all cybersecurity risk and a blocker to projects/initiatives. Cybersecurity could also work with domain owners to draft policies. Domain owners would be accountable for writing policies for their domain and demonstrating compliance to them.
- Cybersecurity in local governments is a public safety risk that needs to be Risk-managed and Safe.
- There are a lot of processes needed to structure the diverse City services. Process information in the Domain Impact worksheet are from the Process Classification Framework® (PCF), The City Government PCF. There is a potential opportunity to leverage the City Government PCF to benchmark services, resulting in improvements in processes and services. Per APQC, the PCF Experience serves as a high-level, industry-neutral enterprise process model that allows organizations to see their business processes from a cross-industry viewpoint.
- The City exhibits a seemingly greater transparency in sharing information about its IT assets compared to the private sector, evident in instances such as Palo Alto Networks customer success story featuring their technology used by the City. However, this abundance of information poses potential risks as threat actors could leverage it for reconnaissance purposes (see MITRE ATT&CK framework T1589, T1590, T1591). Therefore, a well-rounded cybersecurity strategy needs to incorporate the cybersecurity objectives of Educated, Classified, and Risk-Managed. Striking a balance between transparency and security is crucial to maintain the City’s resilience against potential cyber threats.
- The City of Mesa must allocate sufficient resources, if not already, to effectively identify and manage regulatory requirements for its complex environment. This necessitates collaboration, potentially through a committee comprising representatives from IT Security & Risk, the City Attorney’s office, and designated “Domain Owners” (see #5 above) for specific services. Any cybersecurity strategy needs to incorporate the objective of “Compliant.” Below are examples of potential regulatory and standards that may impose requirements for cybersecurity and privacy based on the information utilized and services offered by the City of Mesa. These sources should be carefully considered and integrated into the security strategy to maintain compliance: a) PHI – Health Insurance Portability and Accountability Act; b) PII – Children’s Online Privacy Protection Act, The Electronic Communications Privacy Act, Arizona’s Data-Breach Notification Law; c) Payment Information – The Payment Card Industry Data Security Standard; d) Water Utility – US Environmental Protection Agency Cybersecurity Checklist; e) Arizona Freedom of Information Act; f) US Transportation Security Administration cybersecurity requirements for airports and aircraft operators; g) US Executive Branch Strategies and Orders – National Cybersecurity Strategy, Executive Order 14028, Executive Order 13800. Policy Directive PPD-21; h) US Federal Aviation Agency’s regulations for Unmanned Aircraft System; i)NIST Cybersecurity Framework; j) Criminal Justice Information – FBI’s CJIS Security Policy; k) Cybersecurity Incident – SEC Rules on “Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure by Public Companies.” Obviously, the City of Mesa is not a publicly traded company and these rules don’t apply to the City. However, it might be worthwhile to adopt the SEC framework for handling disclosures in the spirit of transparency if it doesn’t conflict with other laws or regulations.
- Ransomware is a critical concern. Per the Verizon Data Breach report from 2023, ransomware remains the favored approach for disrupting government operations. Several security objectives need to be addressed in response to ransomware: Risk-Managed, Recoverable, Access Controlled, Integrity-Assured, and Educated. Dallas (May 2023 – June 2023) and City of Oakland (February – April 2023) are two examples cities impacted by ransomware attacks. At minimum, the City should, if not already: a) utilize the domain impact worksheet (or similar business architecture modeling or business impact analysis) to initiate the identification of critical services necessitating protection, resilience, and expedited recovery in the event of a ransomware attack; b) evaluate the City’s alignment with CISA’s Stop Ransomware Guide, potentially converting the guidance into a spreadsheet or web application to assess and monitor progress. This evaluation should encompass technology, personnel, and processes; c) encourage cybersecurity technology partners to conduct complimentary ransomware health checks and remediation assessments of their technologies deployed within the City of Mesa’s environment; d) ensure the existence of an up-to-date and tested Incident Response plan, involving key stakeholders such as the City Manager, City Attorney, Mayor, and Councilors. Additionally, safeguard and regularly test the backup and restore infrastructure to ensure its effectiveness in mitigating the impact of a potential ransomware incident. Ensure there is reputable incident response company, like Verizon, Mandiant etc, on retainer to assist with incident response along with appropriate federal and state agencies.
- The City of Mesa should be cognizant of several trends identified in the 2023 Verizon Data Breach Report that are relevant to its security posture. While the report does not provide a breakdown for government levels, the patterns observed, such as system intrusion, basic web attacks, DDoS, social engineering, and miscellaneous errors, are pertinent to municipal entities. Espionage-motivated actors pose a notable threat in this sector, and the persistent issue of collusion between disgruntled internal actors and external entities requires attention. Financially motivated actors and nation states targeting public sectors for information remain a concern, with personal information being the most frequently stolen data type. In response to these threat actors, critical security objectives, including Risk-Managed, Integrity-Assured, and Risk-Aware, must be addressed. The City of Mesa should explore the feasibility of implementing geo-blocking for all web applications, except www.mesaaz.gov, to ensure it continues to support efforts to market and attract individuals and organizations to the city. Additionally, it is advisable for the city to assess its control maturity and capabilities against recognized frameworks such as the CIS Critical Controls and MITRE ATT&CK to ensure a robust and adaptive security posture, especially for applications listed in the “Critical Apps” subdomain. Side note – I like that VERIS has mapped their incident classification patterns to MITRE ATT&CK framework techniques and the CIS Critical Controls
- Similar to other cities, the City of Mesa has placed a strategic emphasis on evolving into a “Smarter City.” As the city progresses towards becoming smarter, several of the previously mentioned Security Objectives remain applicable. The criticality and frequency of cybersecurity incidents are expected to rise, especially as services increasingly rely on interconnected Operational Technology (OT) systems, Information Technology (IT) systems, and Smart City infrastructure. Recognizing the growing complexity and interconnectivity, CISA has offered cybersecurity best practices tailored for and attributes of a trusted for Smart Cities. Consulting and potentially adhering to these best practices is crucial for the City of Mesa to enhance the security posture of its Smart City initiatives.
- Like Rogers Corporation, the City of Mesa has a cloud presence. I would have the same observations for the City of Mesa as those for Rogers Corporation.
Initial questions
- Is the accuracy of the Domain Impact worksheet accurate, or are there crucial elements missing?
- What are critical services and initiatives requiring guidance from cybersecurity?
- What is the risk management process for identity, assessing, addressing etc. risk?
- Who is responsible for collecting regulations etc. and converting them into policies and requirements?
- Is there a dedicated cybersecurity and IT plan for managing attacks involving ransomware?
- Why is business continuity with Cybersecurity?
- How are cybersecurity items on the IT Strategy and Roadmap identified and prioritized?
- How does cybersecurity architecture, enterprise and solution architecture integrate?
- What components of the CIS Critical Security Controls are in place for the Information Technology parent domain in terms of people, process and technology?
- How is the cloud governed? Are there any initiatives involving cloud?
- How is the network segmented?
- How mature is City of Mesa’s Security Operations Capability?
Architecture vs engineering – Good quote
You need both architecture and engineering to ultimately deliver and maintain value for the customer. This is an obvious statement but these two practices are often confused or used interchangeably. I found this definition / statement from Andrew Townley helpful in terms of keeping the “lines” less blurry
If you’re implementing someone else’s design or creating the design of something mentioned in someone else’s design…you’re an engineer..if you’re the one doing the design…or, in most of the cases we find ourselves trying to surface, document and communicate the structure and interconnections of the way our organizations work, identifying critical functions in the context of delivering some kind of thing that ultimately will be recognized by someone as being of “value”..you’re an architect~ Andrew Townley (2023).
How to engage cybersecurity customers
Andrew Townley strikes again with a good piece of advice for engaging with cyber security customers.
1) the conversation isn’t about us, and
2) we need to dial down the jarg-o-meter and industry-speak distortion effects 3x lower than we probably think is necessary.
… Speak in terms of outcomes and objectives – what they want and what things do – rather than what things are, how they work, or using “insider” kool kidz terms that keep your seat at the lunch table with your security colleagues and friends.
Side note – the above is from Andrew’s daily email from https://archistry.com/ (09/28/2021, “When it shouldn’t be dialed up to 11.”)
Architecture – A Definition by Andrew Townley
Listen up architecture fans! I came across a great definition of architecture from Andrew Townley. I received this definition via email. I subscribe to receive emails from him. Enjoy!
The truth – and the problem – actually lies in the power of the thing the word “architecture” itself represents. The simplest version of the definition that is always guaranteed to be true is this one:
“The structure of something.”
Many definitions – including mine – add the words “complex” or “carefully designed” to that definition, but they’re not necessary.
Because everything has an architecture.
Everything.
The question is the degree to which it
- exhibits complexity, and
- has been designed—carefully or otherwise.
Organizations have an architecture, but it isn’t the wires, cables and computers inside it. It’s the collection of governance structures that defines what it is and which work together to deliver the value it creates for its customers. Once you understand this critical point, getting what you want becomes a whole lot easier—
Including security, compliance and true governance.
Zero Trust and Reference Architecture – A definition and attributes
So, I have been doing more in-depth reading on Zero Trust Architecture (ZTA).
Side note – I will share my reading list in a future post.
As I read the Department of Defense’s Zero Trust Reference Architecture, Version 1.0 (February 2021) document, I came across a solid definition of reference architecture:
Reference Architecture is an authoritative source of information
about a specific subject area that guides and constrains the instantiations of multiple
architectures and solutions.
This may see simple, but I bet there is a joke that starts with: two architects walk into a bar to define “reference architecture” and….well, you get the idea.
Below is an excerpt from the scope section of the same document referenced above. I highlighted some key words that can be used to extrapolate other important attributes of a reference architecture.
The content was built to align with the DOD Information Enterprise Architecture (IEA) for consistent mapping of terminology and ease of use as an implementation reference. The scope of the DOD Zero Trust Architecture (ZTA) effort is specifically to determine capabilities and integrations that can be used to successfully advance the Department of Defense Information Network (DODIN) into an interoperable Zero Trust end state. The architecture focused on data-centric design, while maintaining loose coupling across services to maximize interoperability. Other initiatives (e.g. ICAM, Public Key Infrastructure (PKI), etc.) to protect the DODIN are not the subject of this reference architecture but may be shown in some cases to provide additional context for ZTA alignment with DOD IEAs. This Reference Architecture describes Enterprise standards and capabilities. Single products/suites can be adopted to address multiple capabilities. Integrated vendor suites of products rather than individual best of breed components will assist in reducing cost and risk to the government. This document will evolve as requirements, technology, and best practices evolve and mature. Zero Trust promotes individual journey to a collaborative goal of continuous Zero Trust enhancements, while also incorporating best practices, tools, and methodologies of industry.
So, other important attributes of a reference architecture include:
- Aligns with a larger and single Enterprise Architecture
- Uses consistent language and layout for ease of use and orientation by customers
- Defined scope
- Outlines what is not in scope
- Describes standards and capabilities
- Evolves and is updated as requirements, technology and best practices changes, mature or evolve
