- serve and step forward into kitchen
- 3rd shot drives instead of drops when your skill is not good enough, resulting in too many lost points from hitting the ball out or in net
- Moving around at kitchen when dinking instead shuffling side to side or slightly back in a diagonal
- Not in ready position at kitchen with split / horse stance and paddle up
- Doing overhead smash on a ball that is at face level or lower. Needs to be over head or when lower squat down and do a downward punch
The Church of Jesus Christ of Latter-day Saints – General Conference, October 2024 – Themes and Thoughts

Why Now?
I’ve yet to share about my faith on this site, but it’s something deeply personal and central to my life. I am a disciple of Jesus Christ -imperfect, but striving. I belong to the Church of Jesus Christ of Latter-Day Saints (https://www.churchofjesuschrist.org/comeuntochrist). (https://www.churchofjesuschrist.org/comeuntochrist).
Why right something now?
Good question.
I just watched General Conference with my family. If you don’t know, General Conference is
General conference is the worldwide gathering of The Church of Jesus Christ of Latter-day Saints. Twice a year, during the first weekend of April and the first weekend of October, Church leaders from around the world share messages, or sermons, focused on Jesus Christ and His gospel (see (https://www.churchofjesuschrist.org/feature/general-conference?lang=eng)
Side historical note #1: On June 9, 1830, shortly after the April 6, 1830, organization and establishment of the Church, the first conference was held. Only 27 members were present (https://www.churchofjesuschrist.org/church/news/a-brief-history-of-general-conference?lang=eng)
Side historical note #2: The church of Jesus Christ of Latter-day Saints has published histories of their church as well as the journals of Joseph Smith. Both can be found here: https://history.churchofjesuschrist.org/collection/church-history-publications?lang=eng
I often jot down thoughts and key phrases in my bullet journal (https://bulletjournal.com). This time, I felt inspired to share some of these reflections in a blog post, making it easier to selectively share with others. I was also planning to meet with others to discuss our thoughts and impressions, but couldn’t attend as I am on fall break with my family. So, I will share this posting instead of being there in person. Finally, this process of writing and sharing helps me internalize the impressions and words. These internalized words will lead to action, and conversion.
Of course, I’ll keep some thoughts private, as they’re deeply personal.
Quick Statistics
Yes, I like data. There was a total of 34 talks by 34 speakers (excluding the sustaining of church leaders “talk”).
| Name | Age | Sex | Birth Country | Organization |
| Elder Neil L. Andersen | 73 | M | US | Quorum of Twelve Apostles |
| President Emily Belle Freeman | 54 | F | US | Young Women General President |
| Elder Karl D. Hirst | 52 | M | UK | Of the Seventy |
| Elder Dale G. Renlund | 71 | M | US | Quorum of Twelve Apostles |
| Elder David P. Homer | 63 | M | US | Of the Seventy |
| Elder Gregorio E. Casillas | 49 | M | Mexico | Of the Seventy |
| President Dallin H. Oaks | 92 | M | US | First Presidency |
| Elder D. Todd Christofferson | 79 | M | US | Quorum of Twelve Apostles |
| Elder José A. Teixeira | 63 | M | Portugal | Of the Seventy |
| Elder Juan Pablo Villar | 55 | M | Chile | Of the Seventy |
| Elder Patrick Kearon | 63 | M | UK | Quorum of Twelve Apostles |
| Elder David L. Buckner | 61 | M | US | Quorum of Twelve Apostles |
| Elder D. Martin Goury | 60 | M | Côte d’Ivoire | Quorum of Twelve Apostles |
| Elder Aroldo B. Cavalcante | 53 | M | Brazil | Of the Seventy |
| Elder Ulisses Soares | 66 | M | Brazil | Quorum of Twelve Apostles |
| Elder Gerrit W. Gong | 70 | M | US | Quorum of Twelve Apostles |
| Sister Kristin M. Yee | 43 | F | US | Relief Society |
| Elder Kyle S. McKay | 64 | M | US | Of the Seventy |
| Elder Jorge M. Alvarado | 53 | M | Puerto Rico | Of the Seventy |
| Elder David A. Bednar | 72 | M | US | Quorum of Twelve Apostles |
| President Jeffrey R. Holland | 83 | M | US | Quorum of Twelve Apostles |
| Sister Tracy Y. Browning | 48 | F | US | Primary |
| Elder Brook P. Hales | 68 | M | US | Of the Seventy |
| Bishop L. Todd Budge | 64 | M | US | Presiding Bishopric |
| Elder Gary E. Stevenson | 69 | M | US | Quorum of Twelve Apostles |
| Brother Bradley R. Wilcox | 64 | M | US | Young Men |
| President Henry B. Eyring | 91 | M | US | First Presidency |
| Elder Dieter F. Uchtdorf | 83 | M | Czech Republic | Quorum of Twelve Apostles |
| Elder Takashi Wada | 59 | M | Japan | Of the Seventy |
| Elder Ronald A. Rasband | 73 | M | US | Quorum of Twelve Apostles |
| Elder Quentin L. Cook | 84 | M | US | Quorum of Twelve Apostles |
| Elder Rubén V. Alliaud | 58 | M | Argentina | Of the Seventy |
| Elder I. Raymond Egbo | 50 | M | Nigeria | Of the Seventy |
| President Russell M. Nelson | 100 | M | US | First Presidency |
| Summary | |
| Average Age | 66 |
| Percentage Women Speakers | 9% |
| Total US born speakers | 62% |
| Total non-US born speakers | 38% |
| Total Speakers | 34 |
Note – Please see https://newsroom.churchofjesuschrist.org/topic/organizational-structure-of-the-church#:~:text=The%20most%20senior%20apostle%20is,governing%20body%20of%20the%20Church. for more information about each organization listed above.
Word Cloud
To understand the key themes of General Conference, I download all the talks and feed them into a word cloud generator like WordClouds. It highlights the top 50 words and their frequencies.
The top 5 words are:
Here’s what came out of it this time for a word cloud.

I find it beautiful that “hope” and “joy” are also among the top 5 most frequent used words.
If you’re curious whether members of the Church of Jesus Christ of Latter-Day Saints are Christians, just look at the word cloud results: “Christ” was mentioned at least 28 times, making it the 3rd most frequent word in General Conference. Of course, these are just words, but I would also say that many people I know act like Christ did. I encourage you to search other resources that discuss doctrinal similarities and differences between different sects of Christianity, including the Church of Jesus Christ of Latter-Day Saints.
Here are some examples of sources that explain doctrinal differences.
https://rsc.byu.edu/latter-day-saint-essentials/catholicism-mormonism
Other statistics about the Church
https://www.pewresearch.org/religious-landscape-study/database/religious-tradition/mormon/
https://newsroom.churchofjesuschrist.org/facts-and-statistics
“Ask, and it shall be given you; seek, and ye shall find; knock, and it shall be opened unto you” (Luke 11 ver. 9 and 10)
One way I prepare for General Conference is by jotting down 6-10 significant questions that weigh on my mind. These are big, important questions. During each talk, I note thoughts and actions relevant to each question. You could see this as a kind of test, or even applying the scientific method. Each year, I hypothesize that all my questions will be answered either directly or indirectly. Over the past four years of practicing this act of faith, I’ve found answers to every one of my questions. This time, five out of my six questions were answered, and the one that wasn’t had already been addressed previously.
One reason that I am member of Church of Jesus Christ of Latter-Day Saints is because the talks at General Conference help me becoming a better father, citizen, husband and person. I would stop going to Church if the doctrine taught and acted on did not accomplish this in my life.
In this General Conference, the following ideas came to mind about being a better dad and person:
Being a Better Dad:
- Encourage them to ask questions.
- Share the doctrine of Jesus Christ whenever possible in simple terms. Show Christ’s doctrine through actions and use words when necessary.
- Give them opportunities to be still and go into nature, especially amid so many digital distractions.
Being a Better Person:
- Place more effort into growing spiritually. How to measure spiritual growth? Physical growth can be measured in strength and body fat percentage, but for spiritual growth:
- Is it the number of impressions?
- Is it the number of impressions that I acted on?
- Is it the number of things I learned?
- Be still. Make time for quiet reflection and focus on Christ.
- Be consistent with temple attendance.
- Continuously pray for my family to help them navigate the world and resist real temptations of Satan.
General Themes with Associated Quotes from Various Speakers.
*Note – I missed talks on Saturday. The sections below are organized by themes that stood out to me based on words spoken by the speakers. I captured some of these in my journal while others I discovered after re-reading the talks. Each section is followed by a favorite or relevant quote that supports this theme.
Stay the Course and There is Real Opposition (by Elder Holland)
Elder Holland is my favorite apostle.
Elder Holland has a powerful way with words. His messages about perseverance and recognizing the forces that oppose good resonate deeply. What was the quote that stood out to you the most? Here is mine:
So, if sometimes the harder you try, the more difficult it seems to get; if, just as you try to work on your limitations and your shortcomings, you find someone or something determined to challenge your faith; if, as you labor devotedly, you still feel moments of fear wash over you, remember that it has been so for some of the most faithful and marvelous people in every era of time. Also remember that there is a force in the universe determined to oppose every good thing you try to do.
Asking questions is normal, should be encourages, and helps us grow (by Sister Browning)
Didn’t Joseph Smith journey begin by acting on the question found in James?
If any of you lack wisdom, let him ask of God, that giveth to all men liberally, and upbraideth not; and it shall be given him (James 1:5).
We should not discourage people from asking hard spiritual or historical questions about our faith. This is one of my favorite talks and this quote is really good:
Asking questions and searching for meaning are a natural and normal part of our mortal experience. At times, not readily having complete answers can bring us to the edge of our understanding, and those limitations can feel frustrating or overwhelming. Wondrously, Heavenly Father’s plan of happiness for all of us is designed to help us progress despite our limitations and accomplish what we cannot accomplish on our own, even without a complete knowledge of all things. God’s plan is merciful toward the limitations of our humanity; provides us with our Savior, Jesus Christ, to be our Good Shepherd; and inspires us to use our agency to choose Him.
Failure Is Not an Option: Life Helps us Practice True Charity and Patience (by Elder Hales)
One of my favorite quotes:
We will encounter situations that try us and people who enable us to practice true charity and patience….Brothers and sisters, mortality works! It is designed to work! Despite the challenges, heartaches, and difficulties we all face, our loving, wise, and perfect Heavenly Father has designed the plan of happiness such that we are not destined to fail. His plan provides a way for us to rise above our mortal failures. T
Too many distractions. Too much and constant flood of noise. Unplug. Be still (by Elder Budge)
My favorite quotes:
Being still, however, requires more than just making time for the Lord—it requires letting go of our doubtful and fearful thoughts and focusing our hearts and minds on Him…Being still is an act of faith and requires effort. Lectures on Faith states
God desires that we approach our time with Him with the same kind of heartfelt devotion. When we do so, our worship becomes an expression of our love for Him. He yearns for us to commune with Him
On the Sabbath, which in Hebrew means “rest,” what if we were to rest from other cares and to take time to sit quietly with the Lord to pay our devotions unto Him? During our temple worship, what if we were to make a more disciplined effort to pay attention or lingered a little longer in the celestial room in quiet reflection? When our focus is less on doing and more on strengthening our covenant connection with Heavenly Father and Jesus Christ, I testify that each of these sacred moments will be enriched, and we will receive the guidance needed in our personal lives.
Hold on tight. The next 10 years are going to be exciting (by Elder Stevenson)
Favorite quotes:
Between now, 2024, and 2034, we will experience seminal events that will result in extraordinary opportunities to serve, to unite with members and friends, and to introduce The Church of Jesus Christ of Latter-day Saints to more people than ever before.
For you personally, this will be a decade never to be forgotten. But it will be doubly so if you actively strive to become a light unto the world of how the glad tidings of the gospel of Jesus Christ can enrich and enhance not only your lives but also those of your family, friends, and social media followers. You may be wondering how to do this. Prophets of God have taught us this is done through four simple activities, referred to as divinely appointed responsibilities: first, living the gospel of Jesus Christ; second, caring for those in need; third, inviting all to receive the gospel; and fourth, uniting families for eternity. Remarkably, each can be done in the most normal and natural ways.
Teach the Doctrine of Jesus Christ in simple ways and start now since time is so short (by President Eyring)
This is my favorite talk of the entire general conference. There are so many inspirational words.
I thought of every teacher when I heard President Eyring say the following:
As we do our best to teach those we love about the doctrine of Jesus Christ, some may still not respond. Doubts may creep into your mind. You might question whether you know the Savior’s doctrine well enough to teach it effectively. And if you’ve already made attempts to teach it, you may wonder why the positive effects aren’t more visible. Don’t give in to those doubts. Turn to God for help.”
As a father these statements resonated with me:
Some of you may wonder whether it might be better to draw your children closer to you through having fun, or you may ask whether the child may start to feel overwhelmed by your teachings. Instead, we should consider, “With so little time and so few opportunities, what words of doctrine can I share that will strengthen them against the inevitable challenges to their faith?” The words you share today could be the ones they carry with them, and today will soon pass.
Teaching simply allows us to share the saving doctrine early on, while children remain untouched by the deceiver’s temptations that will later confront them, long before the truths they need to learn are drowned out by the noise of social media, peers, and their own personal struggles. We should seize every opportunity to share the teachings of Jesus Christ with children. These teaching moments are precious and far fewer compared to the relentless efforts of opposing forces. For every hour spent instilling doctrine into a child’s life, there are countless hours of opposition filled with messages and images that challenge or ignore those saving truths.
It is tempting to try something new or sensational. But the Holy Ghost will reveal the spirit of truth only as we are cautious and careful not to go beyond teaching true doctrine. One of the surest ways to avoid even getting near false doctrine is to choose to be simple in our teaching. Safety is gained by that simplicity, and little is lost.
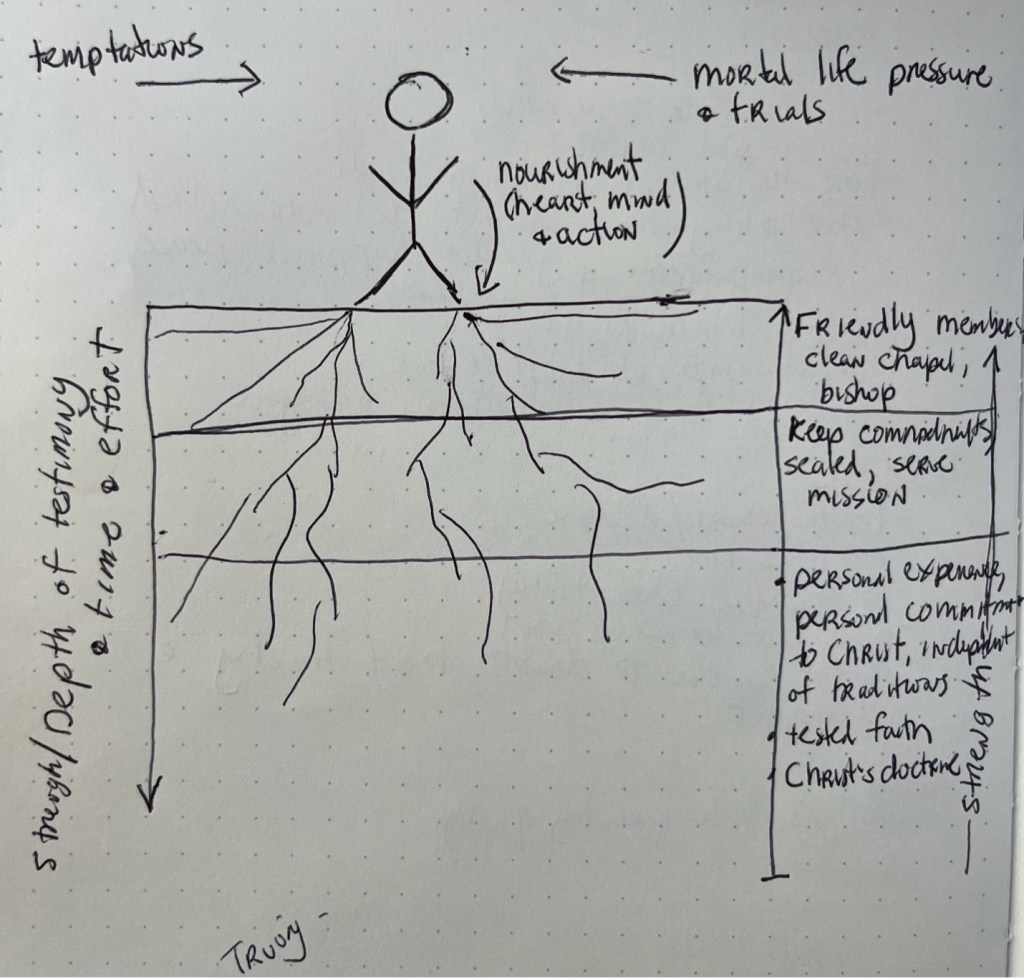
Faith Needs to Be Nourished and Rooted in Christ Not Traditions (by Elder Uchtdorf)
The Church has many traditions and a rich culture. Sometimes, I wonder why we do certain things whether there’s doctrine behind the actions or events. My wife often brings this up as well. Elder Uchtdorf’stalk is a great reminder not to confuse Christ’s doctrine with tradition or to mix up what is eternal with what is not.
Here is a good quote
Faith is strong when it has deep roots in personal experience, personal commitment to Jesus Christ, independent of what our traditions are or what others may say or do.
I also created this simple drawing in my journal after listening to Elder Uchtdorf
Pray always and be uplifting (by Elder Rasband)
Two favorite quotes:
President Nelson has also said: “There has never been a time in the history of the world when knowledge of our Savior is more personally vital and relevant to every human soul. Imagine how quickly the devastating conflicts throughout the world—and those in our individual lives—would be resolved if we all chose to follow Jesus Christ and heed His teachings.”
Brothers and sisters, we need to do more lifting and less murmuring, more upholding the word of the Lord, His ways, and His prophet, who has said: “One of our greatest challenges today is distinguishing between the truths of God and the counterfeits of Satan. That is why the Lord warned us to ‘pray always, … that [we] may conquer Satan, and … escape the hands of the servants of Satan that do uphold [the adversary’s] work’ [Doctrine and Covenants 10:5; emphasis added].”
Reading Bible and Book of Mormon are central to conversion and remaining faithful (by Elder Cook).
Favorite quotes:
We cannot underestimate the significance of sacred scriptures both in conversions and in remaining faithful in the gospel. The ancient prophets described in the Book of Mormon knew about the mission of Jesus Christ and taught His gospel. The Book of Mormon helps us draw closer to God as we learn, understand, and apply its teachings. The Prophet Joseph Smith taught, “A man [or woman] would get nearer to God by abiding by [the book’s] precepts, than by any other book.”
In many significant respects, the Book of Mormon provides fundamental doctrine that enhances and builds upon the Bible. The doctrine of the Atonement of Jesus Christ is a profound example. The Bible provides an accurate account of the mortal ministry of Jesus Christ, including His death and Resurrection. The Book of Mormon is more explicit about the Atonement of Jesus Christ, something prophets explained in detail prior to His death.
President Russell M. Nelson has said, “I promise that as you prayerfully study the Book of Mormon every day, you will make better decisions—every day.” He also promises that if “you daily immerse yourself in the Book of Mormon, you can be immunized against the evils of the day.
… the internet the equivalent of the box full of written material critical of the Church I described earlier, intended to draw you away from God’s truth.
Both long-term members and those newly studying the gospel need to be intentional about what they view. Do not entertain immoral, dishonest, or unrighteous material. If you do, algorithms can lead you down a path that destroys faith and impairs your eternal progression. You can be acted upon positively or negatively. Seek righteousness and avoid dark internet rabbit holes and doomscrolling. Fill your life with positive, righteous ideas; be joyful; have fun but avoid foolishness. There is a difference. The thirteenth article of faith is a marvelous guide. Above all, immerse yourself regularly in the Book of Mormon, which will draw the Spirit into your life and help you discern truth from error.
Ignore the distractions and Focus on Christ (by Elder Egbo)
One favorite quotes:
In a similar way, when we ignore the distractions of the world and focus on Christ and His gospel, we are guaranteed success beyond what we can fully imagine and can feel great joy. President Russell M. Nelson taught: “When the focus of our lives is on … Jesus Christ and His gospel, we can feel joy regardless of what is happening—or not happening—in our lives.”
A Message from A Prophet and Person That is 100 Years old – Study Messages from Conference, Go to the Temple, Rely on Christ and Leverage the Atonement
There are so many memorable statements by President Nelson
Brothers and sisters, now is the time for you and for me to prepare for the Second Coming of our Lord and Savior, Jesus the Christ. Now is the time for us to make our discipleship our highest priority. In a world filled with dizzying distractions, how can we do this?.. Regular worship in the temple will help us.
Study Conference talks:
In this conference, the Lord has spoken to us through His servants. I urge you to study their messages. Use them as a litmus test of what is true and what is not during the next six months.
Promise of a living Prophet:
Here is my promise to you: Every sincere seeker of Jesus Christ will find Him in the temple. You will feel His mercy. You will find answers to your most vexing questions. You will better comprehend the joy of His gospel. I have learned that the most crucial question we each must answer is this: To whom or to what will I give my life? My decision to follow Jesus Christ is the most important decision I have ever made…. Since then our Savior has been the rock upon which I have built my life. That choice has made all the difference! That decision has made so many other decisions easier. That decision has given me purpose and direction. It has also helped me weather the storms of life.
This comment surprised me:
When Wendy and I were on assignment in a distant land, armed robbers put a gun to my head and pulled the trigger. But the gun did not fire. Throughout that experience, both of our lives were threatened. Yet Wendy and I felt an undeniable peace. It was the peace “which passeth all understanding.”
Amazing promises by Christ to all of us:
Please listen to this promise of Jesus Christ to you: “I will be on your right hand and on your left, and my Spirit shall be in your hearts, and mine angels round about you, to bear you up.
Devote time to understand the Atonement
I urge you to devote time each week—for the rest of your life—to increase your understanding of the Atonement of Jesus Christ.
Give your afflictions to Christ
Jesus Christ took upon Himself your sins, your pains, your heartaches, and your infirmities. You do not have to bear them alone! He will forgive you as you repent. He will bless you with what you need. He will heal your wounded soul.As you yoke yourself to Him, your burdens will feel lighter.If you will make and keep covenants to follow Jesus Christ, you will find that the painful moments of your life are temporary. Your afflictions will be “swallowed up in the joy of Christ.”
Dedicated your life to Christ
I call upon you to rededicate your lives to Jesus Christ. I call upon you to help gather scattered Israel and to prepare the world for the Second Coming of the Lord. I call upon you to talk of Christ, testify of Christ, have faith in Christ, and rejoice in Christ!
The Secret to Joy by 100 year old
Come unto Christ and “offer your whole [soul]” to Him.This is the secret to a life of joy!
Best is still coming
The best is yet to come, my dear brothers and sisters, because the Savior is coming again! The best is yet to come because the Lord is hastening His work. The best is yet to come as we fully turn our hearts and our lives to Jesus Christ.
Bonus – Messages from Leadership Training during General Conference.
If you wonder what the Church of Jesus Christ of Latter-Day saints core tenants are, the images below summarizes them (by Elder Patrick Kearon). Each tenant is
as a strand in a cable woven together. Each strand is strong on its own, but as each of these areas works together, there is a combined spiritual strength. There should be a balanced effort in each area as they weave together. Those strands help to sustain and lift a bridge of faith. That bridge helps each member and friend of the Church in their faith journey
The work of the Church is one work centered in Jesus Christ. This one work consists of the five following areas:
- Missionary Work
- Ministering
- Rising Generation
- Temple
- Welfare



What does Lego have to do with Cybersecurity Architecture?
Great question! Despite the risk of spoiling future “ice breakers,” let me share an exercise that answers the question through action. Enough talking—no academic architects needed today!
- Purchase 3-4 identical LEGO kits, each containing between 100-200 pieces. Choose a set that aligns with your organization’s field. For instance, if you’re in healthcare or manufacturing, opt for a car model.
- Unbox all the kits, combine all the pieces into a single bag, mix them thoroughly, and then pour them into a pile.

3) Show a “rules” slide. Below is an example from the last exercise.

4) organize the participants into group of 2-3 people
5) tell people to start.
So, what typically happens next? Well, people love building with LEGO bricks—who doesn’t, right? In every instance I’ve run this exercise, everyone immediately starts grabbing pieces and building something. Why do they do this? Maybe they’re eager to relive fond childhood memories. Perhaps they’re doers who just want to complete the task. Or maybe they feel the competitive pressure of the timer. Regardless, the architects communicate with each other and have a great time. While no one has burst into singing “Everything is Awesome” (see this https://youtu.be/9cQgQIMlwWw?si=ODUGkwCohYu8eeuK), I usually walk around, taking pictures to capture their progress and final creations.




Now, you might be curious about how I handle questions. For this exercise, I used Microsoft Copilot to create a fictional press release between onsemi and Waymo. Depending on the question, I would share this press release.. I have highlighted some key “attributes” within the press release. If you noticed the quotes around “attributes,” you’re right—they refer to SABSA business attributes.
Fictional Press release by Microsoft Co-pilot–
Press Release
onsemi and Waymo Announce Strategic Partnership to Develop Solar-Powered Autonomous Vehicles with Open Design Access
Phoenix, AZ – September 21, 2024 – onsemi (Nasdaq: ON), a leader in intelligent power and sensing technologies, today announced a strategic partnership with Waymo, an autonomous driving technology company, to develop a new generation of solar-powered autonomous, 1 person automobile. This collaboration aims to integrate onsemi’s advanced semiconductor solutions with Waymo’s state-of-the-art autonomous driving systems to create a sustainable and efficient transportation solution. Additionally, the partnership will make the vehicle design available to the public, encouraging innovation and collaboration within the industry.
Hassane El-Khoury, CEO of onsemi, stated:
“We are thrilled to partner with Waymo on this groundbreaking project. This partnership not only represents a significant advancement in sustainable and autonomous transportation but also embodies our commitment to open innovation. By making the design of our solar-powered vehicle available to the public, we aim to foster a collaborative environment where innovators and enthusiasts can contribute to the future of mobility.”
Key Requirements of the Partnership:
- Integration of Solar Technology: The vehicles will be equipped with advanced solar panels to harness renewable energy, significantly reducing the reliance on traditional fuel sources.
- Advanced Semiconductor Solutions: onsemi will provide high-efficiency power management and sensing technologies to optimize the vehicle’s performance and energy consumption.
- Autonomous Driving Systems: Waymo will integrate its latest autonomous driving technology to ensure safe and reliable operation of the vehicles.
- Sustainability Goals: Both companies are committed to achieving significant reductions in carbon emissions and promoting the use of renewable energy in the automotive sector.
- Open Design Access: The partnership will release the vehicle design to the public, allowing engineers, developers, and hobbyists to access and contribute to the development of solar-powered autonomous vehicles.
Innovation and Development: The partnership will focus on continuous innovation and development to push the boundaries of what is possible in autonomous and sustainable transportation.
About onsemi: onsemi (Nasdaq: ON) is driving disruptive innovations to help build a better future. With a focus on automotive and industrial end-markets, the company is accelerating change in megatrends such as vehicle electrification and safety, sustainable energy grids, industrial automation, and 5G and cloud infrastructure. onsemi is headquartered in Phoenix, Arizona, and has a global network of manufacturing facilities, sales offices, and design centers.
About Waymo: Waymo is an autonomous driving technology company with a mission to make it safe and easy for people and things to move around. Since its inception as the Google Self-Driving Car Project in 2009, Waymo has been focused on building the world’s most experienced driver and making it available to everyone.
————————————————————————————————
In this particular exercise, I would have provided the instructions that come with the LEGO set if participants had asked to see the published “open design.”
After the time has elapsed, I ask the following question:
- What does LEGO have to do with cybersecurity architecture?
Here are some answers:
- Efficient, reusable building blocks
- Modularity of the blocks
- Scalability of the blocks.
- Interconnected nature of blocks allow adaptable and efficient models
All of these answers are accurate. However, the key answer is requirements gathering. How do you know what your customer wants, in this case, the CEO of onsemi, if you don’t ask them? If participants had asked “great questions,” as Andrew Townley always advocates, I would have given them pieces of paper with attributes important to Hassane in this fictional scenario.

Of course, you can potentially guess some of the things the customer wants. For example, in this instance, each team created a solar-powered car and a one-person car. You can see the check marks beside the attributes in the picture. However, the teams missed the business objectives of the Waymo partnership: safety and autonomy. How does the final product compare to the imaginary one that Hassan had in mind?

What does this mean? We should always help our customers deliver value. We cannot be roadblocks, even ones made of LEGO bricks. We must always prioritize safety. One way to keep them safe is by ensuring we ask and understand their requirements. This increases the likelihood that the operationalized solution meets the needs of the organization. Don’t get too caught up in the pressure of a “timer.” Don’t get me wrong. We got to deliver and timelines need to be met. Pause, do your homework, ask great questions, and get those requirements documented.
Business Contextual Architecture – Keelson Management, a wholly owned subsidiary of CMA CMG

This is a follow up post to another one that focuses on Port and Terminal Cybersecurity in general. This post focuses on the business contextual architecture of a company responsible for maritime terminal cybersecurity, Keelson Management. This is another use case for The Agile Security System by @Andrew Townley.
Please refer to others postings on The Agile Security System: 1) Overview of The Agile Security System; 2) Overall approach for producing the output for business contextual architectures and initial observations; 3) the efficiency gains via re-use, iterations, and time boxing of this approach; 4) value of this approach – why and help prioritize tactics; and 5) Developing a cybersecurity objectives or business attributes for a cybersecurity strategy based on mitigations to risks to business objectives.
Let me know what you think!
~R&R,
Everyone Needs Some!
Initial Observations
- In the realm of Maritime Transport Systems (MTS), it’s imperative for organizations to designate a Cybersecurity Officer (CySO). The CySO’s key responsibility revolves around developing, revising, and disseminating a “Cyber Annex” to Facility Security Officers. This annex serves as a guarantee that the cybersecurity measures and risk mitigation efforts pertaining to the facility’s physical security and safety are pertinent and adequate. Essentially, it serves as a strategic roadmap to tackle the cybersecurity challenges inherent in MTS. You can find more details about the Cyber Annex at this link: Cyber Annex Guide. It’s worth noting that while the Cyber Annex is a robust strategy, it may not encompass all potential cybersecurity vulnerabilities or remedies. Some might wonder about the necessity of introducing the “CySO” role (vs “CISO” by the US Coast Guard). Nevertheless, for MTS organizations like Keelson, ensuring a cybersecurity strategy aligns with the security objectives of being “Assured” and “Compliant” are paramount.
- Like organizations in other industries, effective management of cyber risk is critical to the success of an MTS organization. A successful cyber-attack can lead to several risks for US ports and terminals. Refer to the CISA diagram, the Port Facility Cybersecurity risk, for a list of cybersecurity risk. “Risk-Managed’ and “Integrity-Assured” are critical security objectives of any cybersecurity strategy.
- Maritime ports are a rich environment for cyber-attacks. For example, a recent study from Rutgers shows various scenarios of physical and cyber-attacks against MTS organization. MTS organizations need to recognize that cyber-attacks translate to real business risk and need to manage it. MTS organizations need to understand that threat actors are “burrowing” into their environments in preparation for future conflicts (refer to minute 30 [ish] of the US House Select Committee on the CCP, “The CCP Cyber Threat to the American Homeland and National Security,” dated 01/31/2024) “Risk-Managed,” and “Educated” (about cyber-attacks on their operating environment) are key objectives.
- The MTS is an industry that has a very visible intersection between the physical and cybersecurity worlds. The compromise of operational technology (OT) ships or systems ashore can result in considerable harm to personal safety and security of ships, ports and marine facilities. Facility Security Assessments (i.e., physical security risk assessments) , as required by the US Coast Guard as part of their Navigation and Vessel Inspection Circular No. 01-20 (NVIC 01-20), includes a review of computing systems and networks; the goal is to understand if cybersecurity vulnerabilities can be exploited to compromise physical controls. As such, US Coast Guard provides recommendations that MTS organizations create a traceability matrix between cybersecurity vulnerabilities and their associated physical security vulnerabilities. US Coast Guard also recommends a traceability matrix between cybersecurity protections and the cybersecurity vulnerabilities they remediate. “Safe” and “Compliant” are important security objectives that need to be part of cybersecurity strategy.
- Practice. Practice. Practice. Incident Response, Business Continuity plans and alert triage playbooks all need to practiced on a regular basis. IR plans must include contacting the FBI, US Coast Guard (i.e., Captain of the Port), and CISA. “Usable,” “Documented”, “Maintained” and “Governed” are critical objectives for any cybersecurity program.
- MTS organizations should use the NIST Cybersecurity Framework to measure effectiveness via a maturity assessment and benchmarking with peers. I recommend hiring a 3rd party to complete an initial maturity assessment and require them to provide a benchmark of the MTS sector. It is critical that any target maturity needs to be calibrated with the risk management and governance of the organization (i.e., NIST CsF Profile). The US Coast Guard recommends using the NIST Cybersecurity Framework (CSF) as the preferred framework for aligning cybersecurity protections, which includes a baseline with various maturity levels. To simplify implementation, I suggest mapping the NIST CSF to CIS Critical Security Controls, incorporating the CIS Controls ICS Implementation Guide for more practical guidance on control implementation. It’s crucial to extend this mapping to the MITRE ATT&CK framework and ensure that assessments encompass the scope of technology deployment, procedures, and staffing levels/skills. Technology is at best ineffective at worst useless without process, correct staffing levels and skill sets. I also recommend reviewing NIST’s website for latest information on NIST CsF 2.0, including the new “Govern” function and Informative References. Today, there is no Community Profile specific to MTS, although there is one for the PNT. MTS organizations heavily use PNT. As such, “Compliant” “Usable” “Governed” and “Effective” are key attributes or security objectives.
- Threat intelligence and collaboration is critical between organizations and entities in the MTS; this also applies between CMA CMG corporation and their subsidiaries. MTS organization should participate in and contribute to the Maritime Transportation System Information Sharing and Analysis Center and the annual Maritime Cybersecurity Summit . The MTS-ISAC publishes an annual report outlining trends that MTS should be aware of. For example, the 2023 report provides the following reasons for increased risk for MTS organizations: a) geopolitical tension; b) inability for MTS organizations (or governments) to counter or pushing nation states or criminals for cyber-attacks. c) economy is driving underemployed or unemployed to cybercrime; d) MTS organizations lag behind in technology and require modernization; and e) an increase in 3rd party integrations. CMA appears to have a threat intelligence capabilities based on their advisories regarding conflicts in world. “Threat-Managed” is an important security objective of Keelson Management cybersecurity strategy.
- Due to the heavy use of OT, OT Cybersecurity needs to be prioritized in terms skill set and process. Need specialization and support for Operational Technology. NIST has published a guide on OT Security (NIST SP 800-32r, According to attacks on OT systems in the maritime industry has increased by 900% since 2017 (in 2021; see https://sustainableworldports.org/wp-content/uploads/IAPH-Cybersecurity-Guidelines-version-1_0.pdf).
- It is imperative for MTS organizations to ensure the defensibility of their cybersecurity programs. I recently engaged in a conversation with a former Chief Information Security Officer (CISO) from a chip manufacturing company. Despite having a budget that surpassed many other organizations, he acknowledged that his organization still faced successful cybersecurity incidents. Every MTS organization must acknowledge the inevitability of compromises. These organizations cannot solely rely on outspending or outskilling threat actors, particularly those backed by nation states. For instance, according to Chris Way, the Director of the FBI, the People’s Republic of China (PRC) boasts the largest hacking program globally, surpassing the combined efforts of all major countries and outnumbering U.S. government hackers 50 to 1 (refer to minute 20 of the Select Committee on the CCP, “The CCP Cyber Threat to the American Homeland and National Security,” dated 01/31/2024). Furthermore, a 2023 MTS-ISAC report highlighted a concerning trend where countries tend to police MTS victims of cyber-attacks and attribute blame to them, rather than holding accountable the threat actor groups responsible. A critical cybersecurity objective of any cybersecurity program is “Auditable.”
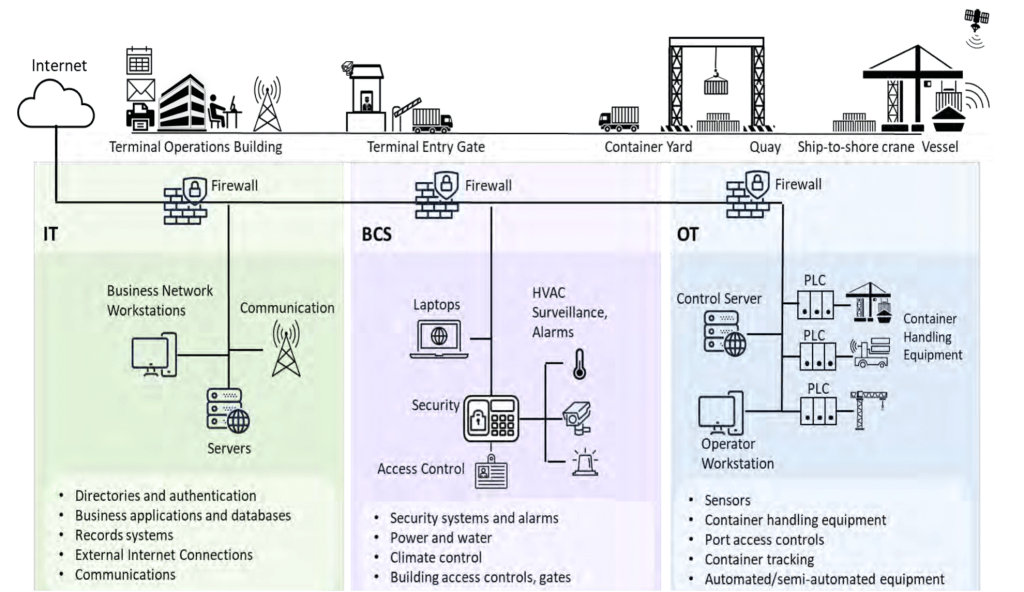
- Network segmentation is critical for MTS organizations. The US Coast Guard published a simple network architecture that highlights an approach to this segmentation.
Initial Questions
- Is the business contextual architecture correct? What is missing?
- Where do requirements for Keelson come from? Below is a listing of sources for potential requirements for a company, like Keelson, operating seaport container terminals in the US. It is imperative for a company to assign a role to consistently review these sources along with others to draft company specific policies and standards and training material. Cybersecurity staff would have to collaborate with legal and compliance teams. Here is a quick list of potential sources: a) International Association of Ports and Harbors (IAPH); b) US Coast Guard (USCG). US Coast Guard has published several guidance documents: i) Navigation and Vessel Inspection Circular (NVIC 01-20) ; ii) Maritime Cybersecurity Assessment and Annex Guide (MCAAG); c) Cybersecurity and Infrastructure Security Agency (CISA); d) Baltic and International Maritime Council (BIMCO); e) International Maritime Organization (IMO).; f) Jones Walker Survey ; g) ISO/IEC 27001; h) Executive Order on Amending Regulations Relating to the Safeguarding of Vessels, Harbors, Ports, and Waterfront Facilities of the United States; h) NIST Cybersecurity Framework (version 2.0); i) Corporate CMA CMG Policies and Standards.
- Are the roles and responsibilities been clearly defined by CMA and Keelson? Why was Keelson originally setup as a wholly owned subsidiary of CMA?
Port and Terminal Cybersecurity
Following President Biden’s recent executive order on “Amending Regulations Relating to the Safeguarding of Vessels, Harbors, Ports, and Waterfront Facilities of the United States” I quickly delved into some research and discovered four valuable resources. Side note, one thing that I love about the cybersecurity field is the opportunity to use your expertise to contribute and make a positive impact across various industries.
Port Facility Cybersecurity Risks Infographic

Jones Walker 2022 Ports and Terminals Cybersecurity Survey

International Association of Ports and Harbors (IAPH)

US Coast Guard – Domestic Ports Division

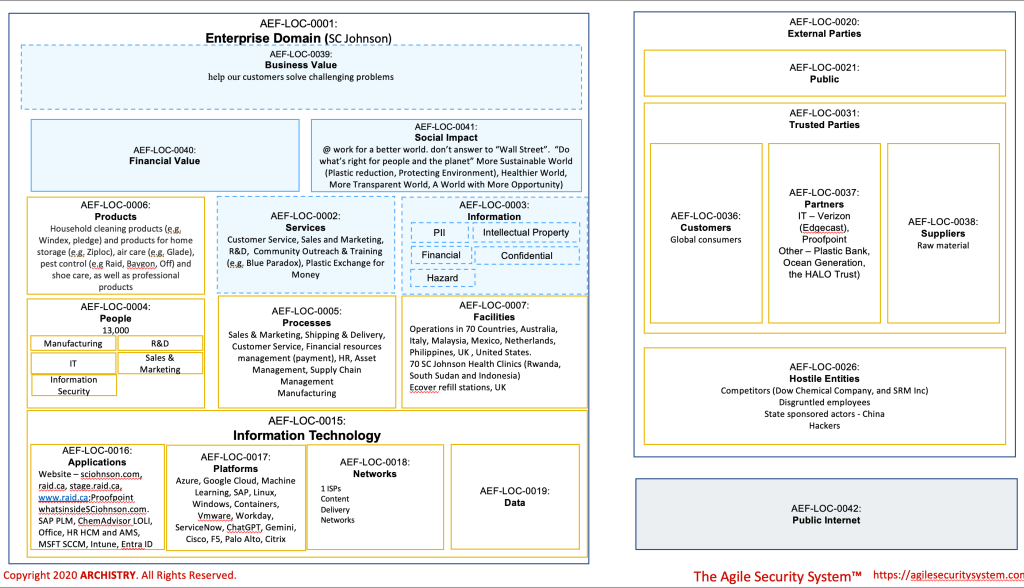
Business Contextual Architecture – SC Johnson & Son, A Manufacturer and the Value of Re-Usable Architecture
Greetings, fellow architect or cybersecurity strategist! Imagine if you had a looming deadline and a meeting scheduled with a stakeholder in just two hours, especially as a newcomer to the company or potentially a new customer, preparation is key.
In tackling this challenge, consider leveraging the Agile Security System (TASS) for a streamlined approach.
Note: for a deeper understanding of the methodology, refer to the insights provided in the Rogers post.
This article, however, won’t introduce new techniques; instead, it underscores the efficacy of TASS, particularly in swiftly delivering a business contextual architecture. The swiftness of TASS is attributed to key factors: simplicity over complicated models in software, a focus on iterations over perfectionism, and a commitment to re-usability.
In terms of re-usability (#3), it’s noteworthy that the domain impact worksheet incorporates elements from another manufacturing company, ON. This re-usability extends beyond the worksheet itself to encompass requirements, risks, mitigations, and even initial observations and questions specific to a particular domain. The versatility of TASS lies in its ability to adapt and apply proven elements across various aspects, facilitating a more efficient and effective approach to cybersecurity strategy. A word of caution though: do not the let beauty of this approach turn you into a “lazy” (not in smart way) and “autopilot architect.”
I prefer to “practice what I preach,” hence I’ve established a two-hour time limit to complete this post. This includes conducting research, developing the domain impact worksheet, formulating observations and questions, and finally, posting the content on the blog. And yes, I leverage ChatGPT to help improve how some of the content is written. Hopefully, ChatGPT doesn’t completely eliminate my personality from the writing!
Let me know what you think!
~R&R,
Everyone Needs Some!
Initial Observations
| Observation | Re-useable | Detailed Information |
| SC Johnson must protect their intellectual property (IP | Yes | See ON Semiconductor posting |
| SC Johnson must have advanced capabilities in intrusion detection, web security, threat intelligence, and training | Yes | See ON Semiconductor posting |
| SC Johnson security, encompassing both facility and infrastructure, including cybersecurity, is crucial for ensuring safety, operational effectiveness and profitability. | Yes | See ON Semiconductor posting |
| SC Johnson must gather and keep up with laws and regulations and translating them into physical, administrative, and technical controls | Yes | See ON Semiconductor posting Note – one unique source of requirements is the US Environmental Protection Agenda List of Lists – Consolidated List of Chemicals |
| SC Johnson must establish an Enterprise Architecture (EA) capability | Yes | See ON Semiconductor posting Note – EA function is even more important in light of SC Johnson strategy to make the world a better place through various initiatives (like Base of the Pyramid Team, Blue Paradox) |
| SC Johnson cybersecurity capabilities must encompass attack surface management and threat intelligence | Yes | See ON Semiconductor posting |
| SC Johnson must have a strategy for cloud governance, process, people and technology. | Yes | See Rogers Posting |
Initial Questions
Re-useable questions for another manufacturer organization
- Is the accuracy of the business architecture confirmed, and is there any essential component missing?
- Does a reference architecture exist for a specific plant that includes cybersecurity requirements? How is the integration handled in the event of a merger with a new company?
- What role does IT and Cybersecurity play in the expansion or installation of a new manufacturing facility?
- In what ways can Cybersecurity support and safeguard Research and Development (R&D) efforts?
- Is there a defined policy or stance regarding Generative AI, and does SC Johnson have an Emerging Technology Committee in place?
Unique Questions
- What critical applications are needed for the key processes identified?
- How integrated are SC Johnson’s partners in terms of their networks or data sharing?
- Has the executive leadership team written a “risk factors” report (like the risk factor section of a SEC filing)?
Humbling….
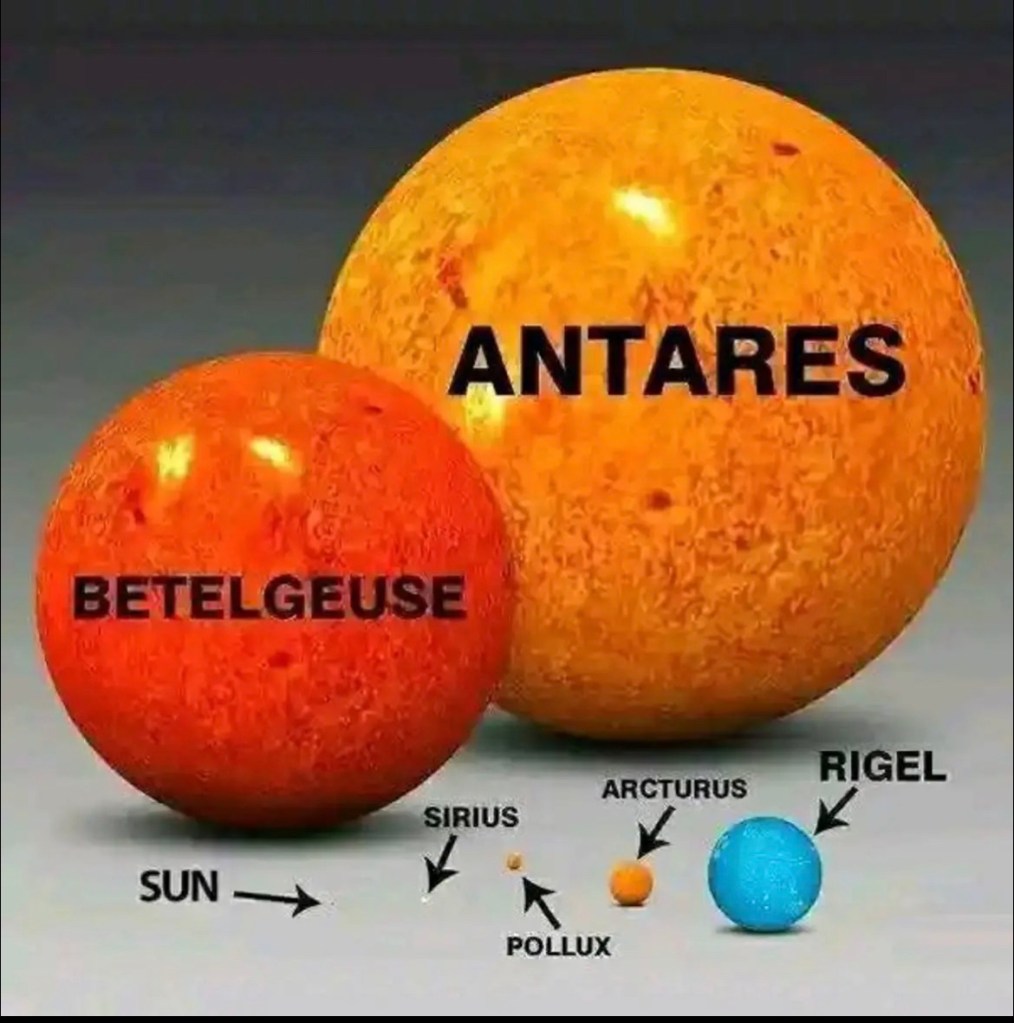
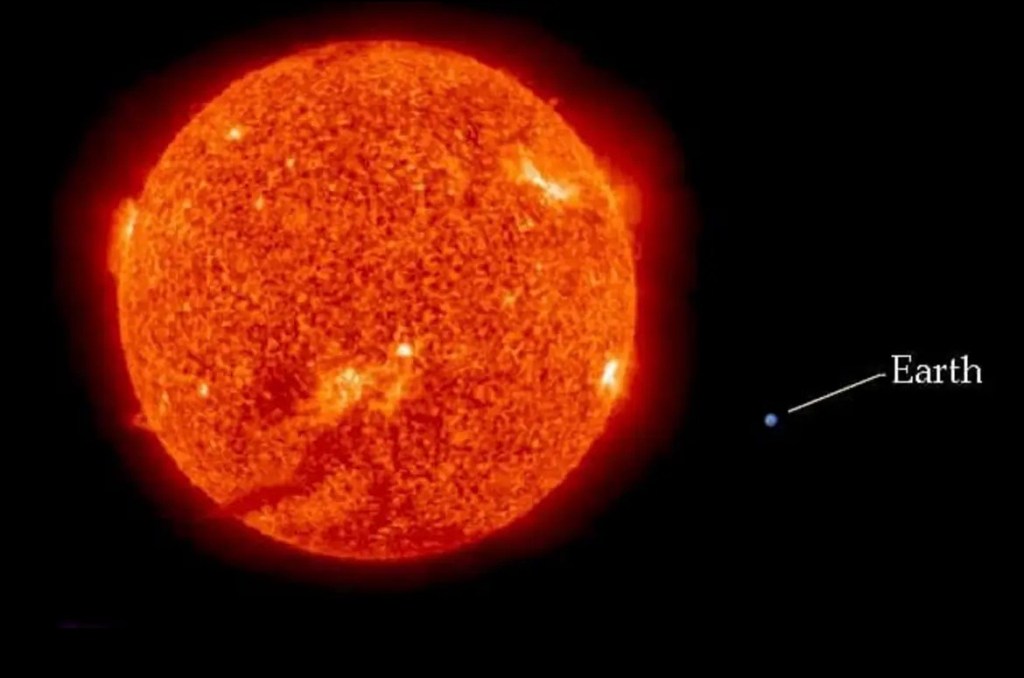
Patagonia cave paintings – 8200 years old

I read this article today, “ These South American cave paintings reveal a surprisingly old tradition” in sciencenews.org. An archaeologist cited in the article states that the “Paint pigments used in the Argentinian cave designs provided the oldest direct dates for rock art in the Americas.” Very cool.
Data Brokers – Consumer Data and Analytics Industries
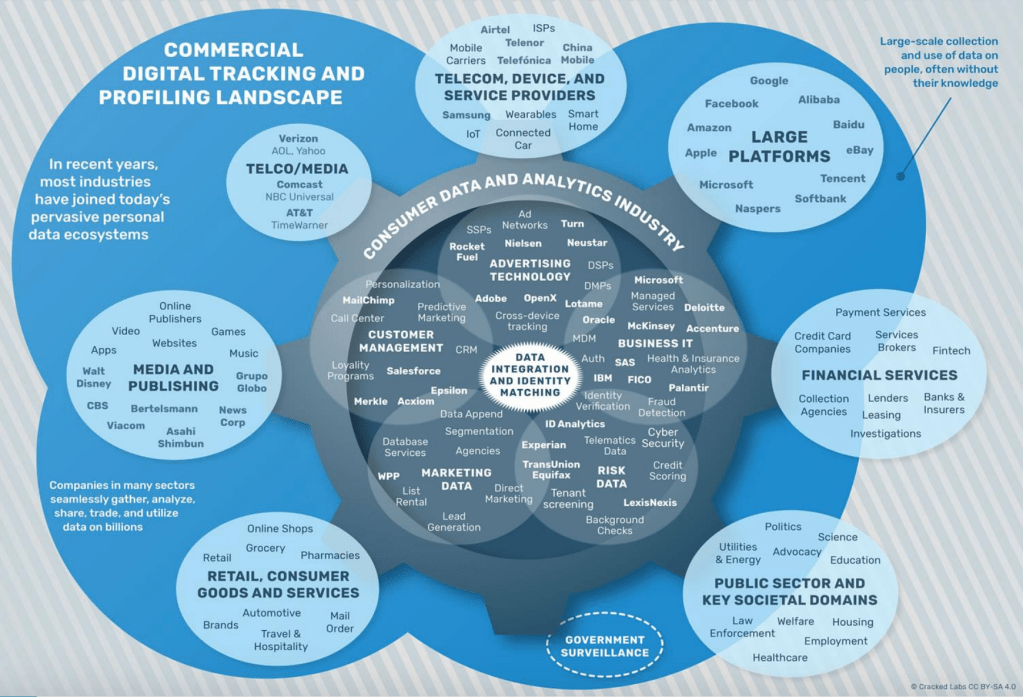
Recently, I came across a LinkedIn post (see Figure 2 below for visual representation) that delved into the intricate journey of data from its inception to consumption.

While it was interesting, it triggered my contemplation on the analogous process concerning our personal data – its collection, analysis, sale, and exploitation for various purposes, notably in marketing. Yes, I’m referring to the realm of the data broker economy. The current estimated size of this economy is $280 to $319 billion depending on source, and is forecasted to go to $545 billion by 2028 according to one source. A relatively recent study concluded that “people don’t understand what marketers are learning about them online and don’t want their data collected, but feel powerless to stop it.” The accompanying graphic (Figure 1) shed some light on the subject, prompting me to delve deeper through additional research into this area.
Business Contextual Architecture – Another Manufacturer Use Case (ON Semiconductor)
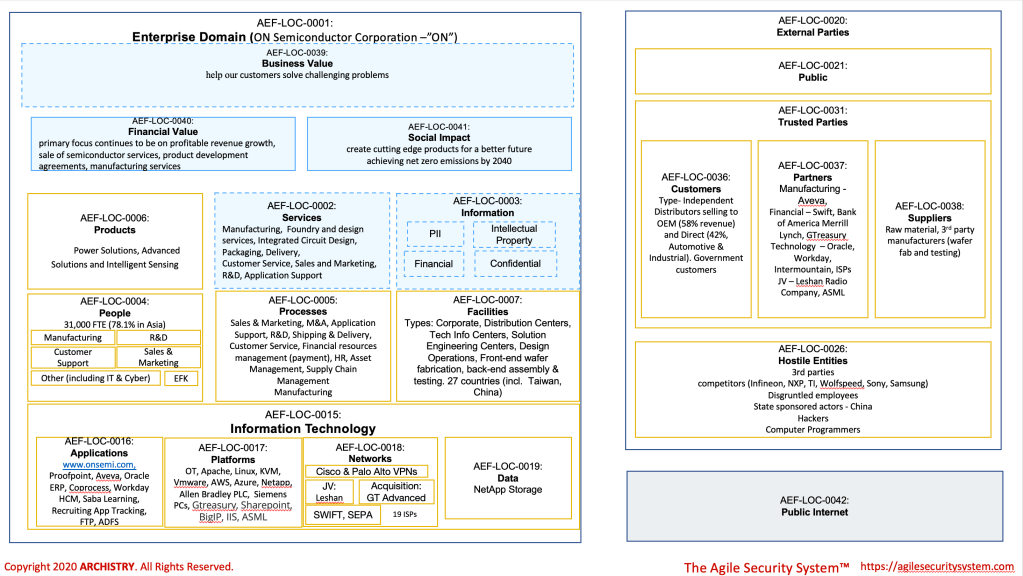
Delve into another instance of harnessing the Agile Security System. This time the focus is on ON Semiconductor. For insights into the methodology, kindly consult the Rogers post. This article will spotlight a couple of ways in which this approach can prove beneficial for individuals in these specific functions:
- Security Operations Center (including cloud)
- Incident Response
- Security Technology Management (i.e. firewall, email, EDR, cloud-native tools etc.)
- Identity Access & Management
- Identity Operations
- Threat hunting & Intelligence
- End point management.
- Forensics
- Detection Engineering
- Data Protection Engineering
- Vulnerability Management
Value of Agile Security System “Artifacts” for Non-Architecture Functions
- It addresses the fundamental “why” behind your role, serving as a source of inspiration. If you haven’t already, consider watching Simon Sinek’s older, but insightful video on this topic (https://youtu.be/Jeg3lIK8lro?si=K9xJGldk1AfQ-zMT) or read his book, “Start with Why.” Utilizing the business contextual architecture enables you to connect your role with the organization’s value. This approach reminds you that your role is an integral part of a larger system or context. Despite the allure and “coolness” of your role (e.g., Penetration Tester, Digital Forensic Examiner, Cloud Security Architect, or Threat Intelligence Analyst), cybersecurity doesn’t operate in isolation; it exists to deliver value. In your role, you contribute to the organization’s success by providing value that aligns with its goals. To put it another way, your role exists to the help the company “win” by helping them managing risk, so they “score points,” “win the game,” “win the championship or season” and be “winners” over decades of time (e.g. IBM, AT&T, GE etc.) What happens to players that don’t help their teams’ win? Yep, they get traded (here is video by Reed Hasting that talks about this analogy).
Side note – I also like Sinek’s view on high performing teams too (https://www.youtube.com/watch?v=zP9jpxitfb4 and https://www.youtube.com/watch?v=PTo9e3ILmms)
At ON, you create value by assisting customers in solving complex problems, contributing to the development of cutting-edge products, supporting the achievement of net-zero emissions by 2040, and facilitating profitable revenue growth. You must help ON do this better and before their competitors. That is it .
This linkage between your cybersecurity function and value becomes clearer when using the Agile Security System’s Baseline Enterprise Perspective ( Figure 2) and the company specific business architecture. The Baseline Enterprise Perspective shows the relationships between the different domains. For example, the “Other” (Figure 1) in the People domain help <<deliver>> services that <<create>> financial, social and business value. Another example is how the “Other” (Figure 1) in the People domain <<manage>> and <<build>> Information Technology, which, in turn, <<supports>> Process and <<represents” Information, which in turn, <<has>> financial value.
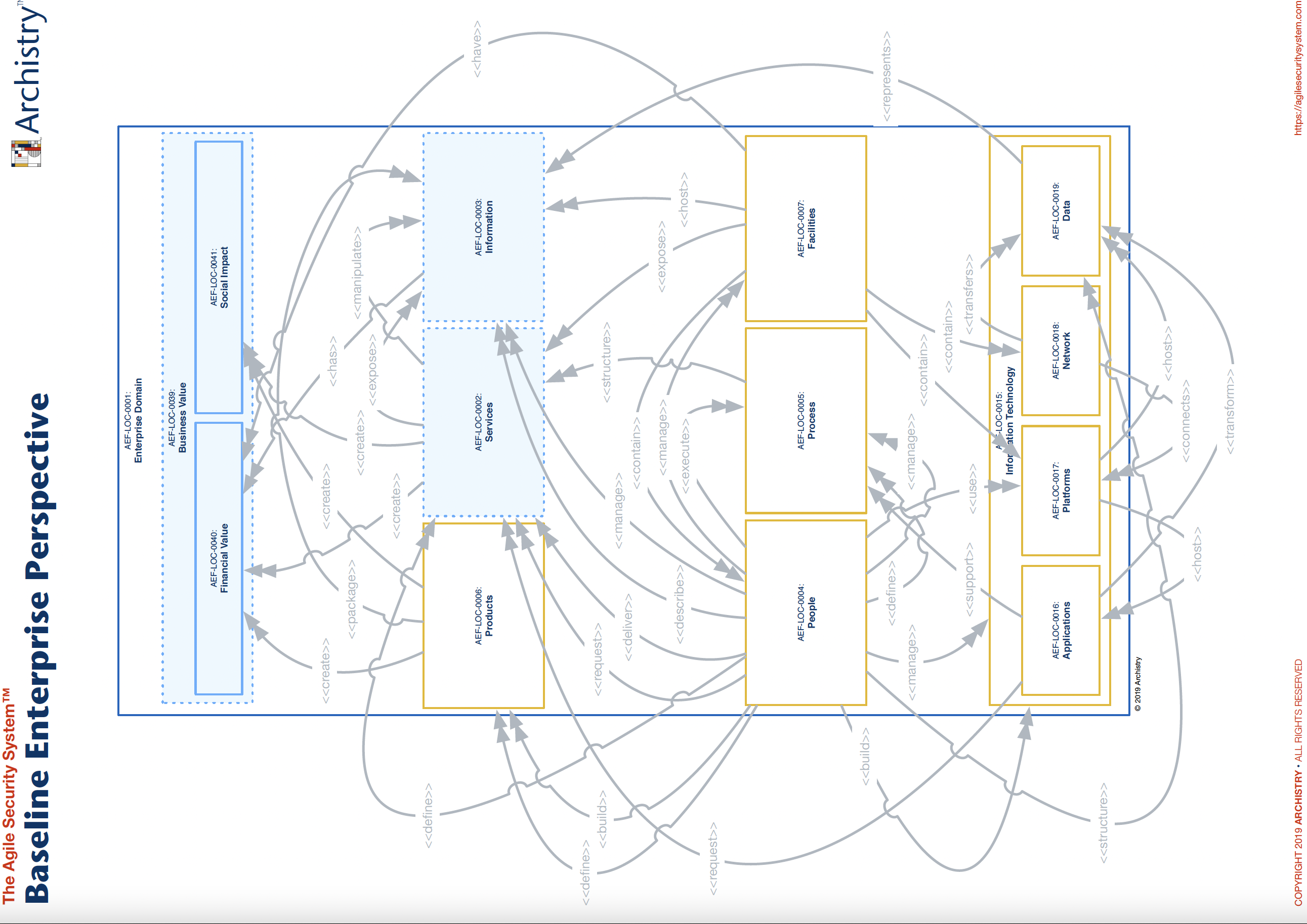
It aids in prioritizing operational activities of your cybersecurity functioning by providing answers to key questions such as:
- Where should I begin vulnerability scanning or requiring continuous scanning?
- What area needs to be “hunted” (and cleared of) for threat actors?
- What alerts and incidents should the SOC and/or IR team prioritize?
- Where should data protection engineering begin focusing their efforts?
- What changes should be assigned a higher risk within the change management process?
- What roles should undergo IAM access reviews?
- What detection alerts should be created by the Detection Engineering team?
- What use cases should the forensics team plan for?
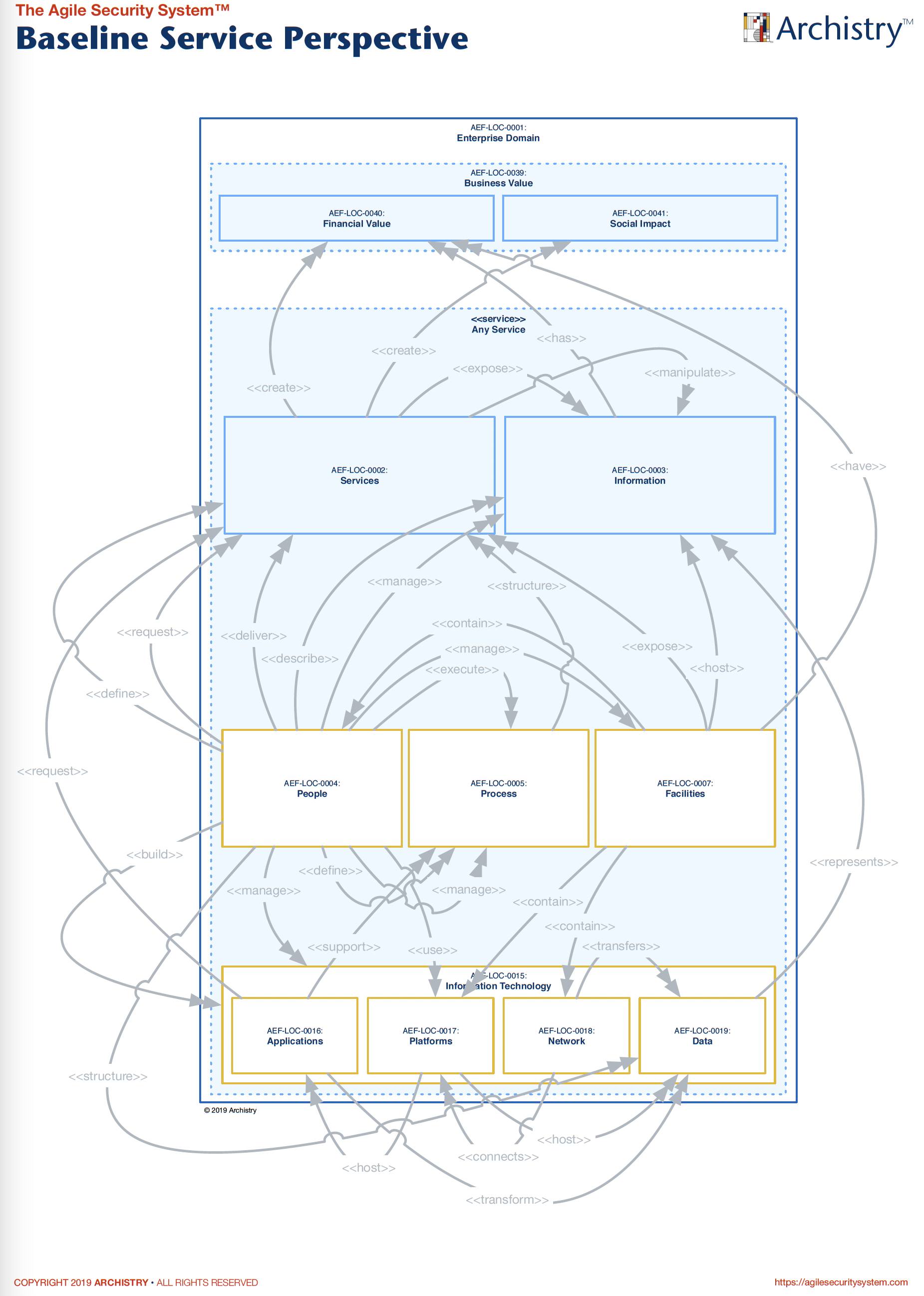
The answer to questions like those above can be uncovered using the architecture depicted in Figure 1 as well as creating an Agile Security System Baseline Service perspective for each service listed in the Services domain (see Figure 3 for the Baseline Service perspective). While the architecture may lack specific technical details like hostnames and IP addresses, obtaining this information and ensuring its accurate linkage to the appropriate parent domain is easily achievable. The primary takeaway is that you now possess an understanding of the crucial services, products, and information contributing to value creation. Our mission is to safeguard and enable this value.
In the case of ON, it’s imperative to conduct vulnerability scans and complete IAM access reviews for applications, platforms, and networks supporting identified in the processes. With the recent acquisitions of “EFK” and “GT Advanced,” can a Zero Trust Network Access solution be deployed to expedite integration while minimizing risks? Does the threat hunting team thoroughly assess the networks associated with EFK and GT Advanced? Do they replicate this exercise when a manufacturing facility expands operations or a new one is built? Did the threat intel team and 3rd party risk team participate in the due diligence process for acquiring EFK and GT Advanced as well as the joint venture with Leshan?
Furthermore, have the detection engineering, data protection engineer, and SOC teams prioritized alerts, DLP rules, and responses for unlikely or unauthorized scenarios? For instance, if an employee in the Sales, Marketing, or IT teams transfers IP information from the US to a Chinese location, how are these situations managed? When the engineering team overseeing firewalls upgrades a firewall responsible for routing/monitoring traffic from a manufacturing process, should this change be considered high-risk even with a high-availability setup? Considering scenarios where an IR or forensic team might need to take a system offline, how do they assess the potential impact of such a decision? IR and forensics teams can refer to the business contextual architecture for insights!
Do you have the responsibility of devising tabletop exercise scenarios? It’s no surprise that you can utilize the business contextual architecture to aid in this task. For example, Understanding that Sales & Marketing services and associated processes play a crucial role in ON’s success, you could focus a tabletop exercise focused on the systems supporting Sales and Marketing processes and what happens if there are unavailable due to a ransomware attack.
Initial Observations
- ON must protect their intellectual property (IP). In the same aforementioned article by Anne Meixner, it is highlighted that individuals with access to critical systems and data within a company can become a security risk, either through intentional malicious actions or unintentional compromise due to human error. An illustrative instance of human error is provided, where engineers inadvertently leaked Samsung trade secrets using ChatGPT. To mitigate such risks, implementing administrative controls such as non-disclosure agreements, confidentiality agreements, trademarks, and educational initiatives becomes crucial. This underscores the need for a well-established insider risk management program to address and mitigate potential threats originating from within the organization. Effectively safeguarding ON’s IP necessitates the integration of security objectives that prioritize Confidentiality, Classification, Threat-Managed, Access-Control, Education, Authorization, Identification Legal, Duty-Segregation, Governance, Risk-Management and Monitoring.
- It is imperative for ON to possess advanced capabilities in intrusion detection, web security, threat intelligence, and training. According to the 2023 Verizon data breach report, surprisingly, only 1% of reported breaches in the Manufacturing sector involved partners, while a significant 90% were attributed to external threat actors. The predominant attack patterns observed were system intrusions, social engineering, and basic web attacks. In the context of motivation, threat actors primarily targeted organizations in the Manufacturing sector for financial gain, espionage, and convenience. Given this landscape, robust threat intelligence capabilities play a pivotal role in comprehending, identifying, and containing attacks driven by espionage motives.The above requires the cybersecurity strategy to incorporate the security objectives that prioritize Confidentiality, , Threat-Managed, Access-Control, Education, Risk-Management and Monitoring.
- A comprehensive vulnerability management program is crucial for ON’s security. Once again, in the article “Securing Chip Manufacturing Against Growing Cyber Threats,” Meixner references Joon Ahn, a vice president in the IT division at Amkor Technology, a company specializing in wafer level and packing assembly. According to Ahn, a notable gap in the semiconductor industry lies in connectivity vulnerabilities. Smart manufacturing technologies heavily rely on connectivity, introducing vulnerabilities as hackers target unsecured network connections to gain access to sensitive systems. The vulnerability management program should be leveraging CVSS 4.0 and have adequate resources assigned to monitor potential vulnerabilities affecting ON’s environment. To address integrity-related security objectives, ON must prioritize Vulnerability-Managed, Change-Managed, Configuration-Managed, Auditable, and Maintenance as essential components of its security strategy.
- As an “outsider” of the semiconductor industry, a semiconductor company like ON has to invest A LOT of capital and operational funds to setup a manufacturer facility. One University of Berkeley study has an estimated range of 3-4 billion US dollars. Every dollar spent on cybersecurity is a dollar taken away from running a manufacturer facility or profit creating service or process. To state the obvious, any security strategy needs to incorporate the security objectives of Cost-Effective and Efficient.
- It seems that ON acknowledges the necessity of incorporating education and awareness into their cybersecurity strategy for both customers and suppliers (see https://www.onsemi.com/company/events/webinars/don-t-let-cybersecurity-become-the-weakest-link-in-the-automotive-system for an example).
- Security, encompassing both facility and infrastructure, including cybersecurity, is crucial for ensuring safety, operational effectiveness and profitability. As articulated in ON’s 10K filing, any inability to use manufacturing facilities, testing facilities, and external manufacturers at anticipated or minimum purchase obligation levels, or a scenario where production capacity expands without a proportional increase in revenue, may lead to fixed costs and operating expenses associated with these facilities and arrangements not being fully absorbed. This could result in elevated average unit costs and diminished gross profits, potentially causing a significant adverse impact on ON’s operational outcomes. Additionally, as Joon Ahn, vice present at Amkor Technology summarized in an article on semiengineering.com, physical security becomes increasingly important as manufacturing facilities become more automated. Unauthorized access to the factory floor can result in equipment damage or theft. Any security strategy needs to incorporate the security objectives of Risk-Managed, Threat-Managed, Access-Controlled, and Interoperable.
- Application security is fundamental. This becomes even more clear and scarier when you read the opinion post by Lumpkin and Levin (2022) in the article “The mother of all ‘zero-days’ – immortal flaws in semiconductor chips.” They state the following:
Every chip starts life as a software program before it is fabricated, mostly in Asia, and mostly in Taiwan, into a chip. The process that transforms design code into “sand in the hand” silicon is just as vulnerable today as consumer applications were in the early 2010s, and for all the same reasons. The impact is deeper and more penetrating because once a chip is compromised, it is nearly impossible to patch. It might be in space or under an ocean. Our enemies know this too.
This means that software flaws needed to be detected and remediated continuously throughout the development lifecycle and iterations. Application security cannot be bolted on, but designed and built in. Any ON cybersecurity strategy must be structured to address the security objectives of Risk-Managed, Awareness, Threat-Managed, Integrity-Assured and Compliant. - Like all organizations, ON must gather and keep up with laws and regulations and translating them into physical, administrative and technical controls. As a manufacturer, ON has several of same sources for requirements as those posted for Rogers. Cybersecurity strategy must be organized to address the security objectives of Auditable, Legal and Compliant. Here are some potential sources for cybersecurity requirements: a) United States Patent and Trademark Office; b) United States Uniform Trade Secrets Act; c) United States Sarbanes-Oxley Act of 2002; d) European Union’s General Data Protection Regulation; e) United States Patent and Trademark Office; f) Canadian Bill C-27; g) SEMI E187 and SEMI E188 Standards; h) Creating Helpful Incentives to Produce Semiconductors and Science Act; i) United States Inflation Reduction Act; j)the International Traffic in Arms Regulation promulgated under the Arms Export Control Act (“ITAR”; k) United States Foreign Corrupt Practices Act (“FCPA”); l) anti-boycott provisions of the U.S. Export Administration Act; m) United States Responsible Business Alliance (“RBA”) Code of Conduct United States; n) FCPA (anti-corruption laws); o) NIST 800-171.
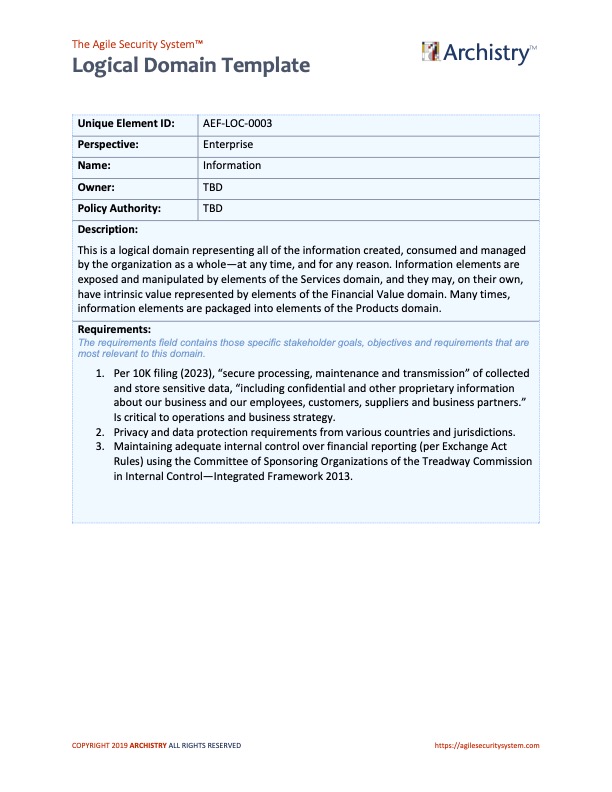
If you’re curious about how the Agile Security System manages requirements engineering, please consult the Figures 5, 6, and 7 provided below (prior to the questions section). It’s important to note that these figures are not complete and would require further iterations. The figure also only show the first page of the domain analysis worksheet too. This aspect is notably robust within the Agile Security System, allowing you to follow a set of requirements, objectives, or goals within a specific domain, along with their associated risks and mitigations. Notably, these aspects directly correspond to cybersecurity strategy. This process can be defined as the threat modeling of the business context. As per the threat modeling manifesto, the process involves addressing four key questions: a) What are we building (requirements, goals, objectives)?; b) What could go wrong (risks)? c) How do we plan to address it (mitigations)? d) Have we done an adequate job? The final question involves a “gut check” to evaluate the documentation. Ideally, all questions are collaboratively answered by the team, avoiding dependence on a singular “hero threat modeler.” - Establishing an Enterprise Architecture (EA) capability is imperative to provide a systematic approach to processes and architecture. This is essential for supporting the design and implementation of a new manufacturing facility and the integration of new companies. The EA capability should also encompass cybersecurity architecture.
As noted in ON’s 10K filing from 2022, if ON is
unable to successfully integrate new strategic acquisitions, which could materially adversely affect our business, results of operations and financial condition. Per Successful acquisitions and alliances in our industry require, among other things, efficient integration and aligning of product offerings and manufacturing operations and coordination of sales and marketing and research and development efforts, often in markets or regions in which we have less experience. Risks related to successful integration of an acquisition include, but are not limited to: (1) the ability to integrate information technology and other systems; (2) issues not discovered in our due diligence
ON’s cybersecurity strategy must incorporate the security objectives of Risk-Managed, Threat-Managed, Integrity-Assured, Governed, Efficient , Cost-Effective, Monitored, Usable and Adaptable. - For a global company, effective cybersecurity capabilities must encompass attack surface management and threat intelligence. ON seems to operate with 19 Internet Service Providers (ISPs) and 102 visible endpoints on the internet (including 4 DNS servers and 4 email servers via Proofpoint). It is crucial to vigilantly monitor the contraction and expansion of this attack surface to identify potential weaknesses, such as configuration errors or systems without system owners
- Like Rogers Corporation and the City of Mesa, ON has a cloud presence (in AWS). It appears that may be migrating their website, www.onsemi.com to AWS (beta-www.onsemi.com). I have the same observations for ON as those for Rogers Corporation.
- ON must retain highly skilled personnel, and its cybersecurity program should not be overly burdensome to the extent that employees choose to leave the company. It is crucial that the cybersecurity program at ON is competitive, efficient, effective, and user-friendly to avoid making it overly burdensome and cumbersome.
- ON provides products to companies in the industrial sector, contributing to the development of more intelligent cities, factories, and buildings. The demand for cybersecurity in product delivery is expected to rise as ON’s “smart” technologies continue to expand, and the company adopts its own technology in its manufacturing facilities. Another term used to describe a more intelligent factory is Industry 4.0 (or the 4th Industrial Revolution), as per ChatGPT 3.5, involving the integration of digital technologies, the Internet of Things, artificial intelligence, and data analytics into the industrial process. Clearly, as manufacturing processes become more digitized and interconnected for ON and its customers and suppliers, solving cybersecurity challenges becomes crucial.
- Managing Third-Party/Supply Chain Risks is crucial. This involves overseeing aspects such as monitoring, access control, incident response, and governance. However, it’s crucial to strike a balance; third-party risk management practices and processes must not become so burdensome that companies are disinclined to engage in business collaborations. The reliance of manufacturing and operations on third-party facilities, suppliers of raw materials, and software is significant. Identifying alternative manufacturers and suppliers can be a time-consuming and expensive endeavor, often complicated by a limited pool of qualified providers. Collaboration and a well-practiced incident response plan are vital when dealing with connections to third parties. It’s essential to limit exposure and prioritize containment. This means restricting third-party access to a specific set of resources, thereby minimizing the potential impact. Regular validation of access, following a zero-trust approach, adds an extra layer of security and assurance.
The article, “Securing Chip Manufacturing Against Growing Cyber Threats” by Anne Meixner states that 60% to 90%, of impactful security issues stem from suppliers. This is, in part, due to a growing level of interdependency among companies in this industry, and ON is likely no exception. As the Meixner’s article summarizes the current situation of 3rd party interdependency.
Where methodologies and standards do exist for security, they often are confusing, cumbersome, and incomplete. There are plenty of gaps, particularly among some of the smaller suppliers of IP, equipment, and materials, where security remains primitive at best. This is partly due to the fact that in the past, much of the focus was on vulnerabilities in chips and chipmakers. But there is an increasingly high level of interdependency between companies in the semiconductor industry. The number of interactions is growing as complexity increases, and as chip designs become increasingly heterogeneous.
Figure 4 provides a conceptual view of the interdependency the semiconductor industry Change Managed, Monitored, Risk-Managed, Access-Controlled, Threat-Monitored, Threat Management, Governed, and Vetted are key attributes that need to be part of any cybersecurity strategy.

Initial Questions
- Is the accuracy of the business architecture confirmed, and are there any essential elements missing?
- Does a reference architecture exist for a specific manufacturing facilities that includes cybersecurity requirements? That is, business knows the cost associated with the cybersecurity infrastructure and tools for a facility. Has IT provided a BOM for the different facility types? Does cybersecurity have a process to on-board a facility into their processes?
- How are risk management and policy governance handled? Is ON the culture open an approach similar to one discussed for the City of Mesa?
- How is the integration handled in the event of a merger with a new company?
- What is the logistics process for transporting products between facilities? For instance, how are silicon wafers manufactured in the Czech Republic transported to a facility in another company? How are these protected?
- What role does IT and Cybersecurity play in the expansion or installation of a new manufacturing facility?
- In what ways can Cybersecurity support and safeguard Research and Development (R&D) efforts?
- The prevalence of VPN connections is notable. With 23 internet-accessible VPN endpoints (23 out of 103, or 22%), what is the reason for this high number?
- Is there an ongoing project to transition http://www.onsemi.com to AWS (beta-www.onsemi.com, 23.22.192.64)? Has AWS been design with their cloud adoption framework? Does the SOC use cloud native tools or 3rd party tools for security cloud operations?
- Is there representation from ON at Semicon West, and is Semicon West considered a reputable conference?
- Is there a defined policy or stance regarding Generative AI, and does ON have an Emerging Technology Committee in place?
- Is ON following the guidance from the NSA? Is it applicable?

