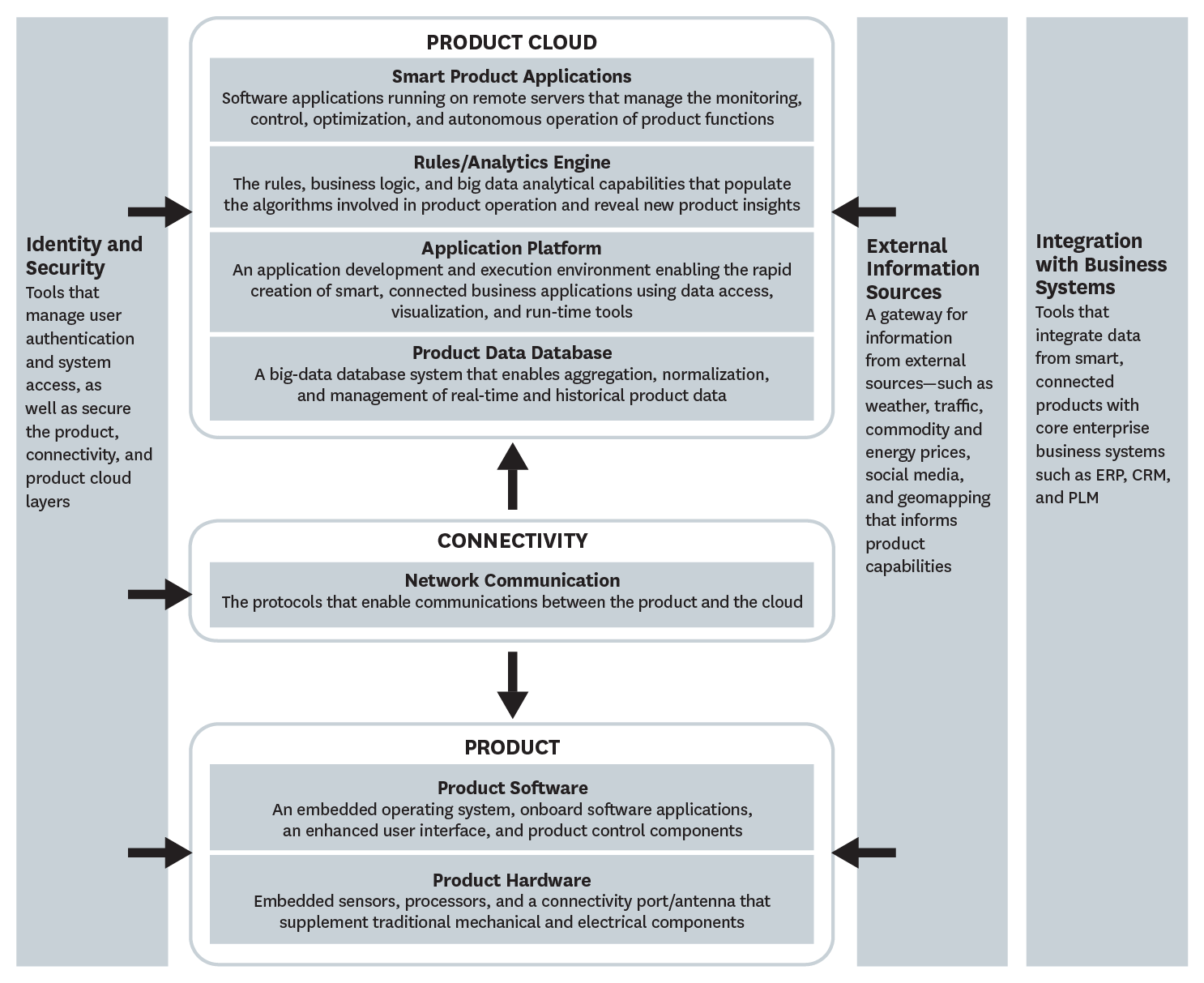
I randomly (can you say “squirrel”) came across article entitled, ” How Smart, Connected Products Are Transforming Companies.” The article has an interesting architecture or new technology stack for handling smart, connected products. It requires companies to build and support an entirely new technology infrastructure. The entire article is a really good read.
The authors writes about the need for security:
Until recently, IT departments in manufacturing companies have been largely responsible for safeguarding firms’ data centers, business systems, computers, and networks. With the advent of smart, connected devices, the game changes dramatically. The job of ensuring IT security now cuts across all functions.
Every smart, connected device may be a point of network access, a target of hackers, or a launchpad for cyberattacks. Smart, connected products are widely distributed, exposed, and hard to protect with physical measures. Because the products themselves often have limited processing power, they cannot support modern security hardware and software.
Smart, connected products share some familiar vulnerabilities with IT in general. For example, they are susceptible to the same type of denial-of-service attack that overwhelms servers and networks with a flood of access requests. However, these products have major new points of vulnerability, and the impact of intrusions can be more severe. Hackers can take control of a product or tap into the sensitive data that moves between it, the manufacturer, and the customer. On the TV program 60 Minutes, DARPA demonstrated how a hacker could gain complete control of a car’s acceleration and braking, for example. The risk posed by hackers penetrating aircraft, automobiles, medical equipment, generators, and other connected products could be far greater than the risks from a breach of a business e-mail server.
Customers expect products and their data to be safe. So a firm’s ability to provide security is becoming a key source of value—and a potential differentiator. Customers with extraordinary security needs, such as the military and defense organizations, may demand special services.
Security will affect multiple functions. Clearly the IT function will continue to play a central role in identifying and implementing best practices for data and network security. And the need to embed security in product design is crucial. Risk models must consider threats across all potential points of access: the device, the network to which it is connected, and the product cloud. New risk-mitigation techniques are emerging: The U.S. Food and Drug Administration, for example, has mandated that layered authentication levels and timed usage sessions be built into all medical devices to minimize the risk to patients. Security can also be enhanced by giving customers or users the ability to control when data is transmitted to the cloud and what type of data the manufacturer can collect. Overall, knowledge and best practices for security in a smart, connected world are rapidly evolving.
Data privacy and the fair exchange of value for data are also increasingly important to customers. Creating data policies and communicating them to customers is becoming a central concern of legal, marketing, sales and service, and other departments. In addition to addressing customers’ privacy concerns, data policies must reflect ever-stricter government regulations and transparently define the type of data collected and how it will be used internally and by third parties.
…Shared Responsibility for Security.
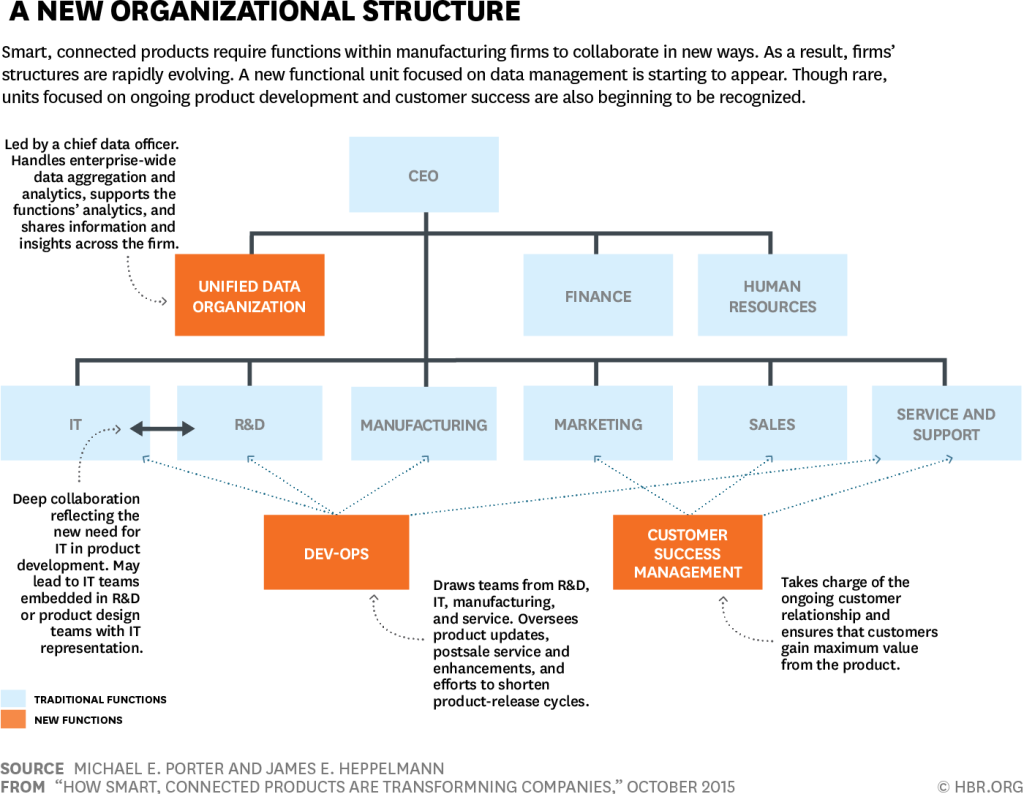
In most companies, executive oversight of security is in flux. Security may report to the chief information officer, the chief technology officer, the chief data officer, or the chief compliance officer. Whatever the leadership structure, security cuts across product development, dev-ops, IT, the field service group, and other units. Especially strong collaboration among R&D, IT, and the data organization is essential. The data organization, along with IT, will normally be responsible for securing product data, defining user access and rights protocols, and identifying and complying with regulations. The R&D and dev-ops teams will take the lead on reducing vulnerabilities in the physical product. IT and R&D will often be jointly responsible for maintaining and protecting the product cloud and its connections to the product. However, the organizational model for managing security is still being written.
The authors continue with implications for organizational structure (i.e., The Takeaways)