Why Now?
I’ve yet to share about my faith on this site, but it’s something deeply personal and central to my life. I am a disciple of Jesus Christ -imperfect, but striving. I belong to the Church of Jesus Christ of Latter-Day Saints (https://www.churchofjesuschrist.org/comeuntochrist). (https://www.churchofjesuschrist.org/comeuntochrist).
Why right something now?
Good question.
I just watched General Conference with my family. If you don’t know, General Conference is
General conference is the worldwide gathering of The Church of Jesus Christ of Latter-day Saints. Twice a year, during the first weekend of April and the first weekend of October, Church leaders from around the world share messages, or sermons, focused on Jesus Christ and His gospel (see (https://www.churchofjesuschrist.org/feature/general-conference?lang=eng)
Side historical note #1: On June 9, 1830, shortly after the April 6, 1830, organization and establishment of the Church, the first conference was held. Only 27 members were present (https://www.churchofjesuschrist.org/church/news/a-brief-history-of-general-conference?lang=eng)
Side historical note #2: The church of Jesus Christ of Latter-day Saints has published histories of their church as well as the journals of Joseph Smith. Both can be found here: https://history.churchofjesuschrist.org/collection/church-history-publications?lang=eng
I often jot down thoughts and key phrases in my bullet journal (https://bulletjournal.com). This time, I felt inspired to share some of these reflections in a blog post, making it easier to selectively share with others. I was also planning to meet with others to discuss our thoughts and impressions, but couldn’t attend as I am on fall break with my family. So, I will share this posting instead of being there in person. Finally, this process of writing and sharing helps me internalize the impressions and words. These internalized words will lead to action, and conversion.
Of course, I’ll keep some thoughts private, as they’re deeply personal.
Quick Statistics
Yes, I like data. There was a total of 34 talks by 34 speakers (excluding the sustaining of church leaders “talk”).
| Name | Age | Sex | Birth Country | Organization |
| Elder Neil L. Andersen | 73 | M | US | Quorum of Twelve Apostles |
| President Emily Belle Freeman | 54 | F | US | Young Women General President |
| Elder Karl D. Hirst | 52 | M | UK | Of the Seventy |
| Elder Dale G. Renlund | 71 | M | US | Quorum of Twelve Apostles |
| Elder David P. Homer | 63 | M | US | Of the Seventy |
| Elder Gregorio E. Casillas | 49 | M | Mexico | Of the Seventy |
| President Dallin H. Oaks | 92 | M | US | First Presidency |
| Elder D. Todd Christofferson | 79 | M | US | Quorum of Twelve Apostles |
| Elder José A. Teixeira | 63 | M | Portugal | Of the Seventy |
| Elder Juan Pablo Villar | 55 | M | Chile | Of the Seventy |
| Elder Patrick Kearon | 63 | M | UK | Quorum of Twelve Apostles |
| Elder David L. Buckner | 61 | M | US | Quorum of Twelve Apostles |
| Elder D. Martin Goury | 60 | M | Côte d’Ivoire | Quorum of Twelve Apostles |
| Elder Aroldo B. Cavalcante | 53 | M | Brazil | Of the Seventy |
| Elder Ulisses Soares | 66 | M | Brazil | Quorum of Twelve Apostles |
| Elder Gerrit W. Gong | 70 | M | US | Quorum of Twelve Apostles |
| Sister Kristin M. Yee | 43 | F | US | Relief Society |
| Elder Kyle S. McKay | 64 | M | US | Of the Seventy |
| Elder Jorge M. Alvarado | 53 | M | Puerto Rico | Of the Seventy |
| Elder David A. Bednar | 72 | M | US | Quorum of Twelve Apostles |
| President Jeffrey R. Holland | 83 | M | US | Quorum of Twelve Apostles |
| Sister Tracy Y. Browning | 48 | F | US | Primary |
| Elder Brook P. Hales | 68 | M | US | Of the Seventy |
| Bishop L. Todd Budge | 64 | M | US | Presiding Bishopric |
| Elder Gary E. Stevenson | 69 | M | US | Quorum of Twelve Apostles |
| Brother Bradley R. Wilcox | 64 | M | US | Young Men |
| President Henry B. Eyring | 91 | M | US | First Presidency |
| Elder Dieter F. Uchtdorf | 83 | M | Czech Republic | Quorum of Twelve Apostles |
| Elder Takashi Wada | 59 | M | Japan | Of the Seventy |
| Elder Ronald A. Rasband | 73 | M | US | Quorum of Twelve Apostles |
| Elder Quentin L. Cook | 84 | M | US | Quorum of Twelve Apostles |
| Elder Rubén V. Alliaud | 58 | M | Argentina | Of the Seventy |
| Elder I. Raymond Egbo | 50 | M | Nigeria | Of the Seventy |
| President Russell M. Nelson | 100 | M | US | First Presidency |
| Summary | |
| Average Age | 66 |
| Percentage Women Speakers | 9% |
| Total US born speakers | 62% |
| Total non-US born speakers | 38% |
| Total Speakers | 34 |
Note – Please see https://newsroom.churchofjesuschrist.org/topic/organizational-structure-of-the-church#:~:text=The%20most%20senior%20apostle%20is,governing%20body%20of%20the%20Church. for more information about each organization listed above.
Word Cloud
To understand the key themes of General Conference, I download all the talks and feed them into a word cloud generator like WordClouds. It highlights the top 50 words and their frequencies.
The top 5 words are:
Here’s what came out of it this time for a word cloud.

I find it beautiful that “hope” and “joy” are also among the top 5 most frequent used words.
If you’re curious whether members of the Church of Jesus Christ of Latter-Day Saints are Christians, just look at the word cloud results: “Christ” was mentioned at least 28 times, making it the 3rd most frequent word in General Conference. Of course, these are just words, but I would also say that many people I know act like Christ did. I encourage you to search other resources that discuss doctrinal similarities and differences between different sects of Christianity, including the Church of Jesus Christ of Latter-Day Saints.
Here are some examples of sources that explain doctrinal differences.
https://rsc.byu.edu/latter-day-saint-essentials/catholicism-mormonism
Other statistics about the Church
https://www.pewresearch.org/religious-landscape-study/database/religious-tradition/mormon/
https://newsroom.churchofjesuschrist.org/facts-and-statistics
“Ask, and it shall be given you; seek, and ye shall find; knock, and it shall be opened unto you” (Luke 11 ver. 9 and 10)
One way I prepare for General Conference is by jotting down 6-10 significant questions that weigh on my mind. These are big, important questions. During each talk, I note thoughts and actions relevant to each question. You could see this as a kind of test, or even applying the scientific method. Each year, I hypothesize that all my questions will be answered either directly or indirectly. Over the past four years of practicing this act of faith, I’ve found answers to every one of my questions. This time, five out of my six questions were answered, and the one that wasn’t had already been addressed previously.
One reason that I am member of Church of Jesus Christ of Latter-Day Saints is because the talks at General Conference help me becoming a better father, citizen, husband and person. I would stop going to Church if the doctrine taught and acted on did not accomplish this in my life.
In this General Conference, the following ideas came to mind about being a better dad and person:
Being a Better Dad:
- Encourage them to ask questions.
- Share the doctrine of Jesus Christ whenever possible in simple terms. Show Christ’s doctrine through actions and use words when necessary.
- Give them opportunities to be still and go into nature, especially amid so many digital distractions.
Being a Better Person:
- Place more effort into growing spiritually. How to measure spiritual growth? Physical growth can be measured in strength and body fat percentage, but for spiritual growth:
- Is it the number of impressions?
- Is it the number of impressions that I acted on?
- Is it the number of things I learned?
- Be still. Make time for quiet reflection and focus on Christ.
- Be consistent with temple attendance.
- Continuously pray for my family to help them navigate the world and resist real temptations of Satan.
General Themes with Associated Quotes from Various Speakers.
*Note – I missed talks on Saturday. The sections below are organized by themes that stood out to me based on words spoken by the speakers. I captured some of these in my journal while others I discovered after re-reading the talks. Each section is followed by a favorite or relevant quote that supports this theme.
Stay the Course and There is Real Opposition (by Elder Holland)
Elder Holland is my favorite apostle.
Elder Holland has a powerful way with words. His messages about perseverance and recognizing the forces that oppose good resonate deeply. What was the quote that stood out to you the most? Here is mine:
So, if sometimes the harder you try, the more difficult it seems to get; if, just as you try to work on your limitations and your shortcomings, you find someone or something determined to challenge your faith; if, as you labor devotedly, you still feel moments of fear wash over you, remember that it has been so for some of the most faithful and marvelous people in every era of time. Also remember that there is a force in the universe determined to oppose every good thing you try to do.
Asking questions is normal, should be encourages, and helps us grow (by Sister Browning)
Didn’t Joseph Smith journey begin by acting on the question found in James?
If any of you lack wisdom, let him ask of God, that giveth to all men liberally, and upbraideth not; and it shall be given him (James 1:5).
We should not discourage people from asking hard spiritual or historical questions about our faith. This is one of my favorite talks and this quote is really good:
Asking questions and searching for meaning are a natural and normal part of our mortal experience. At times, not readily having complete answers can bring us to the edge of our understanding, and those limitations can feel frustrating or overwhelming. Wondrously, Heavenly Father’s plan of happiness for all of us is designed to help us progress despite our limitations and accomplish what we cannot accomplish on our own, even without a complete knowledge of all things. God’s plan is merciful toward the limitations of our humanity; provides us with our Savior, Jesus Christ, to be our Good Shepherd; and inspires us to use our agency to choose Him.
Failure Is Not an Option: Life Helps us Practice True Charity and Patience (by Elder Hales)
One of my favorite quotes:
We will encounter situations that try us and people who enable us to practice true charity and patience….Brothers and sisters, mortality works! It is designed to work! Despite the challenges, heartaches, and difficulties we all face, our loving, wise, and perfect Heavenly Father has designed the plan of happiness such that we are not destined to fail. His plan provides a way for us to rise above our mortal failures. T
Too many distractions. Too much and constant flood of noise. Unplug. Be still (by Elder Budge)
My favorite quotes:
Being still, however, requires more than just making time for the Lord—it requires letting go of our doubtful and fearful thoughts and focusing our hearts and minds on Him…Being still is an act of faith and requires effort. Lectures on Faith states
God desires that we approach our time with Him with the same kind of heartfelt devotion. When we do so, our worship becomes an expression of our love for Him. He yearns for us to commune with Him
On the Sabbath, which in Hebrew means “rest,” what if we were to rest from other cares and to take time to sit quietly with the Lord to pay our devotions unto Him? During our temple worship, what if we were to make a more disciplined effort to pay attention or lingered a little longer in the celestial room in quiet reflection? When our focus is less on doing and more on strengthening our covenant connection with Heavenly Father and Jesus Christ, I testify that each of these sacred moments will be enriched, and we will receive the guidance needed in our personal lives.
Hold on tight. The next 10 years are going to be exciting (by Elder Stevenson)
Favorite quotes:
Between now, 2024, and 2034, we will experience seminal events that will result in extraordinary opportunities to serve, to unite with members and friends, and to introduce The Church of Jesus Christ of Latter-day Saints to more people than ever before.
For you personally, this will be a decade never to be forgotten. But it will be doubly so if you actively strive to become a light unto the world of how the glad tidings of the gospel of Jesus Christ can enrich and enhance not only your lives but also those of your family, friends, and social media followers. You may be wondering how to do this. Prophets of God have taught us this is done through four simple activities, referred to as divinely appointed responsibilities: first, living the gospel of Jesus Christ; second, caring for those in need; third, inviting all to receive the gospel; and fourth, uniting families for eternity. Remarkably, each can be done in the most normal and natural ways.
Teach the Doctrine of Jesus Christ in simple ways and start now since time is so short (by President Eyring)
This is my favorite talk of the entire general conference. There are so many inspirational words.
I thought of every teacher when I heard President Eyring say the following:
As we do our best to teach those we love about the doctrine of Jesus Christ, some may still not respond. Doubts may creep into your mind. You might question whether you know the Savior’s doctrine well enough to teach it effectively. And if you’ve already made attempts to teach it, you may wonder why the positive effects aren’t more visible. Don’t give in to those doubts. Turn to God for help.”
As a father these statements resonated with me:
Some of you may wonder whether it might be better to draw your children closer to you through having fun, or you may ask whether the child may start to feel overwhelmed by your teachings. Instead, we should consider, “With so little time and so few opportunities, what words of doctrine can I share that will strengthen them against the inevitable challenges to their faith?” The words you share today could be the ones they carry with them, and today will soon pass.
Teaching simply allows us to share the saving doctrine early on, while children remain untouched by the deceiver’s temptations that will later confront them, long before the truths they need to learn are drowned out by the noise of social media, peers, and their own personal struggles. We should seize every opportunity to share the teachings of Jesus Christ with children. These teaching moments are precious and far fewer compared to the relentless efforts of opposing forces. For every hour spent instilling doctrine into a child’s life, there are countless hours of opposition filled with messages and images that challenge or ignore those saving truths.
It is tempting to try something new or sensational. But the Holy Ghost will reveal the spirit of truth only as we are cautious and careful not to go beyond teaching true doctrine. One of the surest ways to avoid even getting near false doctrine is to choose to be simple in our teaching. Safety is gained by that simplicity, and little is lost.
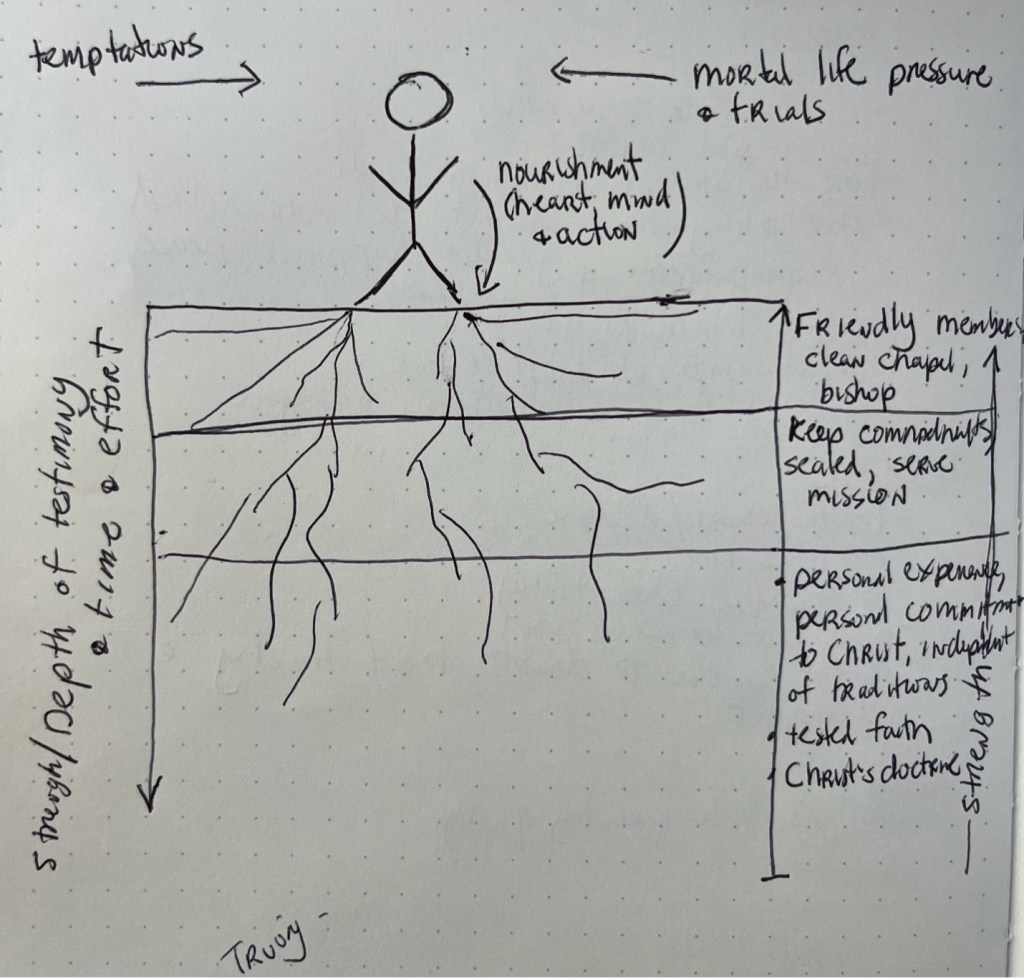
Faith Needs to Be Nourished and Rooted in Christ Not Traditions (by Elder Uchtdorf)
The Church has many traditions and a rich culture. Sometimes, I wonder why we do certain things whether there’s doctrine behind the actions or events. My wife often brings this up as well. Elder Uchtdorf’stalk is a great reminder not to confuse Christ’s doctrine with tradition or to mix up what is eternal with what is not.
Here is a good quote
Faith is strong when it has deep roots in personal experience, personal commitment to Jesus Christ, independent of what our traditions are or what others may say or do.
I also created this simple drawing in my journal after listening to Elder Uchtdorf
Pray always and be uplifting (by Elder Rasband)
Two favorite quotes:
President Nelson has also said: “There has never been a time in the history of the world when knowledge of our Savior is more personally vital and relevant to every human soul. Imagine how quickly the devastating conflicts throughout the world—and those in our individual lives—would be resolved if we all chose to follow Jesus Christ and heed His teachings.”
Brothers and sisters, we need to do more lifting and less murmuring, more upholding the word of the Lord, His ways, and His prophet, who has said: “One of our greatest challenges today is distinguishing between the truths of God and the counterfeits of Satan. That is why the Lord warned us to ‘pray always, … that [we] may conquer Satan, and … escape the hands of the servants of Satan that do uphold [the adversary’s] work’ [Doctrine and Covenants 10:5; emphasis added].”
Reading Bible and Book of Mormon are central to conversion and remaining faithful (by Elder Cook).
Favorite quotes:
We cannot underestimate the significance of sacred scriptures both in conversions and in remaining faithful in the gospel. The ancient prophets described in the Book of Mormon knew about the mission of Jesus Christ and taught His gospel. The Book of Mormon helps us draw closer to God as we learn, understand, and apply its teachings. The Prophet Joseph Smith taught, “A man [or woman] would get nearer to God by abiding by [the book’s] precepts, than by any other book.”
In many significant respects, the Book of Mormon provides fundamental doctrine that enhances and builds upon the Bible. The doctrine of the Atonement of Jesus Christ is a profound example. The Bible provides an accurate account of the mortal ministry of Jesus Christ, including His death and Resurrection. The Book of Mormon is more explicit about the Atonement of Jesus Christ, something prophets explained in detail prior to His death.
President Russell M. Nelson has said, “I promise that as you prayerfully study the Book of Mormon every day, you will make better decisions—every day.” He also promises that if “you daily immerse yourself in the Book of Mormon, you can be immunized against the evils of the day.
… the internet the equivalent of the box full of written material critical of the Church I described earlier, intended to draw you away from God’s truth.
Both long-term members and those newly studying the gospel need to be intentional about what they view. Do not entertain immoral, dishonest, or unrighteous material. If you do, algorithms can lead you down a path that destroys faith and impairs your eternal progression. You can be acted upon positively or negatively. Seek righteousness and avoid dark internet rabbit holes and doomscrolling. Fill your life with positive, righteous ideas; be joyful; have fun but avoid foolishness. There is a difference. The thirteenth article of faith is a marvelous guide. Above all, immerse yourself regularly in the Book of Mormon, which will draw the Spirit into your life and help you discern truth from error.
Ignore the distractions and Focus on Christ (by Elder Egbo)
One favorite quotes:
In a similar way, when we ignore the distractions of the world and focus on Christ and His gospel, we are guaranteed success beyond what we can fully imagine and can feel great joy. President Russell M. Nelson taught: “When the focus of our lives is on … Jesus Christ and His gospel, we can feel joy regardless of what is happening—or not happening—in our lives.”
A Message from A Prophet and Person That is 100 Years old – Study Messages from Conference, Go to the Temple, Rely on Christ and Leverage the Atonement
There are so many memorable statements by President Nelson
Brothers and sisters, now is the time for you and for me to prepare for the Second Coming of our Lord and Savior, Jesus the Christ. Now is the time for us to make our discipleship our highest priority. In a world filled with dizzying distractions, how can we do this?.. Regular worship in the temple will help us.
Study Conference talks:
In this conference, the Lord has spoken to us through His servants. I urge you to study their messages. Use them as a litmus test of what is true and what is not during the next six months.
Promise of a living Prophet:
Here is my promise to you: Every sincere seeker of Jesus Christ will find Him in the temple. You will feel His mercy. You will find answers to your most vexing questions. You will better comprehend the joy of His gospel. I have learned that the most crucial question we each must answer is this: To whom or to what will I give my life? My decision to follow Jesus Christ is the most important decision I have ever made…. Since then our Savior has been the rock upon which I have built my life. That choice has made all the difference! That decision has made so many other decisions easier. That decision has given me purpose and direction. It has also helped me weather the storms of life.
This comment surprised me:
When Wendy and I were on assignment in a distant land, armed robbers put a gun to my head and pulled the trigger. But the gun did not fire. Throughout that experience, both of our lives were threatened. Yet Wendy and I felt an undeniable peace. It was the peace “which passeth all understanding.”
Amazing promises by Christ to all of us:
Please listen to this promise of Jesus Christ to you: “I will be on your right hand and on your left, and my Spirit shall be in your hearts, and mine angels round about you, to bear you up.
Devote time to understand the Atonement
I urge you to devote time each week—for the rest of your life—to increase your understanding of the Atonement of Jesus Christ.
Give your afflictions to Christ
Jesus Christ took upon Himself your sins, your pains, your heartaches, and your infirmities. You do not have to bear them alone! He will forgive you as you repent. He will bless you with what you need. He will heal your wounded soul.As you yoke yourself to Him, your burdens will feel lighter.If you will make and keep covenants to follow Jesus Christ, you will find that the painful moments of your life are temporary. Your afflictions will be “swallowed up in the joy of Christ.”
Dedicated your life to Christ
I call upon you to rededicate your lives to Jesus Christ. I call upon you to help gather scattered Israel and to prepare the world for the Second Coming of the Lord. I call upon you to talk of Christ, testify of Christ, have faith in Christ, and rejoice in Christ!
The Secret to Joy by 100 year old
Come unto Christ and “offer your whole [soul]” to Him.This is the secret to a life of joy!
Best is still coming
The best is yet to come, my dear brothers and sisters, because the Savior is coming again! The best is yet to come because the Lord is hastening His work. The best is yet to come as we fully turn our hearts and our lives to Jesus Christ.
Bonus – Messages from Leadership Training during General Conference.
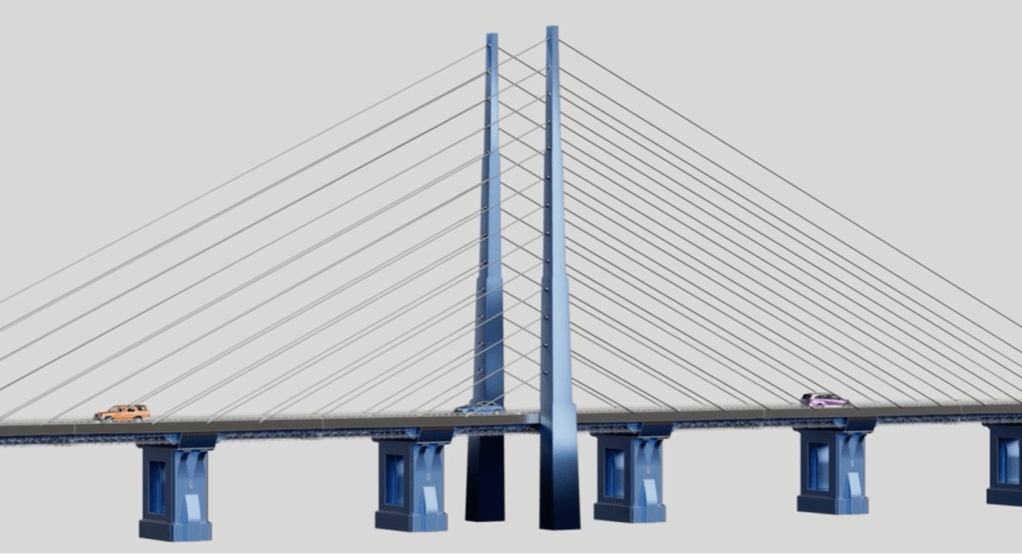
If you wonder what the Church of Jesus Christ of Latter-Day saints core tenants are, the images below summarizes them (by Elder Patrick Kearon). Each tenant is
as a strand in a cable woven together. Each strand is strong on its own, but as each of these areas works together, there is a combined spiritual strength. There should be a balanced effort in each area as they weave together. Those strands help to sustain and lift a bridge of faith. That bridge helps each member and friend of the Church in their faith journey
The work of the Church is one work centered in Jesus Christ. This one work consists of the five following areas:
- Missionary Work
- Ministering
- Rising Generation
- Temple
- Welfare