
This is a follow up post to another one that focuses on Port and Terminal Cybersecurity in general. This post focuses on the business contextual architecture of a company responsible for maritime terminal cybersecurity, Keelson Management. This is another use case for The Agile Security System by @Andrew Townley.
Please refer to others postings on The Agile Security System: 1) Overview of The Agile Security System; 2) Overall approach for producing the output for business contextual architectures and initial observations; 3) the efficiency gains via re-use, iterations, and time boxing of this approach; 4) value of this approach – why and help prioritize tactics; and 5) Developing a cybersecurity objectives or business attributes for a cybersecurity strategy based on mitigations to risks to business objectives.
Let me know what you think!
~R&R,
Everyone Needs Some!
Initial Observations
- In the realm of Maritime Transport Systems (MTS), it’s imperative for organizations to designate a Cybersecurity Officer (CySO). The CySO’s key responsibility revolves around developing, revising, and disseminating a “Cyber Annex” to Facility Security Officers. This annex serves as a guarantee that the cybersecurity measures and risk mitigation efforts pertaining to the facility’s physical security and safety are pertinent and adequate. Essentially, it serves as a strategic roadmap to tackle the cybersecurity challenges inherent in MTS. You can find more details about the Cyber Annex at this link: Cyber Annex Guide. It’s worth noting that while the Cyber Annex is a robust strategy, it may not encompass all potential cybersecurity vulnerabilities or remedies. Some might wonder about the necessity of introducing the “CySO” role (vs “CISO” by the US Coast Guard). Nevertheless, for MTS organizations like Keelson, ensuring a cybersecurity strategy aligns with the security objectives of being “Assured” and “Compliant” are paramount.
- Like organizations in other industries, effective management of cyber risk is critical to the success of an MTS organization. A successful cyber-attack can lead to several risks for US ports and terminals. Refer to the CISA diagram, the Port Facility Cybersecurity risk, for a list of cybersecurity risk. “Risk-Managed’ and “Integrity-Assured” are critical security objectives of any cybersecurity strategy.
- Maritime ports are a rich environment for cyber-attacks. For example, a recent study from Rutgers shows various scenarios of physical and cyber-attacks against MTS organization. MTS organizations need to recognize that cyber-attacks translate to real business risk and need to manage it. MTS organizations need to understand that threat actors are “burrowing” into their environments in preparation for future conflicts (refer to minute 30 [ish] of the US House Select Committee on the CCP, “The CCP Cyber Threat to the American Homeland and National Security,” dated 01/31/2024) “Risk-Managed,” and “Educated” (about cyber-attacks on their operating environment) are key objectives.
- The MTS is an industry that has a very visible intersection between the physical and cybersecurity worlds. The compromise of operational technology (OT) ships or systems ashore can result in considerable harm to personal safety and security of ships, ports and marine facilities. Facility Security Assessments (i.e., physical security risk assessments) , as required by the US Coast Guard as part of their Navigation and Vessel Inspection Circular No. 01-20 (NVIC 01-20), includes a review of computing systems and networks; the goal is to understand if cybersecurity vulnerabilities can be exploited to compromise physical controls. As such, US Coast Guard provides recommendations that MTS organizations create a traceability matrix between cybersecurity vulnerabilities and their associated physical security vulnerabilities. US Coast Guard also recommends a traceability matrix between cybersecurity protections and the cybersecurity vulnerabilities they remediate. “Safe” and “Compliant” are important security objectives that need to be part of cybersecurity strategy.
- Practice. Practice. Practice. Incident Response, Business Continuity plans and alert triage playbooks all need to practiced on a regular basis. IR plans must include contacting the FBI, US Coast Guard (i.e., Captain of the Port), and CISA. “Usable,” “Documented”, “Maintained” and “Governed” are critical objectives for any cybersecurity program.
- MTS organizations should use the NIST Cybersecurity Framework to measure effectiveness via a maturity assessment and benchmarking with peers. I recommend hiring a 3rd party to complete an initial maturity assessment and require them to provide a benchmark of the MTS sector. It is critical that any target maturity needs to be calibrated with the risk management and governance of the organization (i.e., NIST CsF Profile). The US Coast Guard recommends using the NIST Cybersecurity Framework (CSF) as the preferred framework for aligning cybersecurity protections, which includes a baseline with various maturity levels. To simplify implementation, I suggest mapping the NIST CSF to CIS Critical Security Controls, incorporating the CIS Controls ICS Implementation Guide for more practical guidance on control implementation. It’s crucial to extend this mapping to the MITRE ATT&CK framework and ensure that assessments encompass the scope of technology deployment, procedures, and staffing levels/skills. Technology is at best ineffective at worst useless without process, correct staffing levels and skill sets. I also recommend reviewing NIST’s website for latest information on NIST CsF 2.0, including the new “Govern” function and Informative References. Today, there is no Community Profile specific to MTS, although there is one for the PNT. MTS organizations heavily use PNT. As such, “Compliant” “Usable” “Governed” and “Effective” are key attributes or security objectives.
- Threat intelligence and collaboration is critical between organizations and entities in the MTS; this also applies between CMA CMG corporation and their subsidiaries. MTS organization should participate in and contribute to the Maritime Transportation System Information Sharing and Analysis Center and the annual Maritime Cybersecurity Summit . The MTS-ISAC publishes an annual report outlining trends that MTS should be aware of. For example, the 2023 report provides the following reasons for increased risk for MTS organizations: a) geopolitical tension; b) inability for MTS organizations (or governments) to counter or pushing nation states or criminals for cyber-attacks. c) economy is driving underemployed or unemployed to cybercrime; d) MTS organizations lag behind in technology and require modernization; and e) an increase in 3rd party integrations. CMA appears to have a threat intelligence capabilities based on their advisories regarding conflicts in world. “Threat-Managed” is an important security objective of Keelson Management cybersecurity strategy.
- Due to the heavy use of OT, OT Cybersecurity needs to be prioritized in terms skill set and process. Need specialization and support for Operational Technology. NIST has published a guide on OT Security (NIST SP 800-32r, According to attacks on OT systems in the maritime industry has increased by 900% since 2017 (in 2021; see https://sustainableworldports.org/wp-content/uploads/IAPH-Cybersecurity-Guidelines-version-1_0.pdf).
- It is imperative for MTS organizations to ensure the defensibility of their cybersecurity programs. I recently engaged in a conversation with a former Chief Information Security Officer (CISO) from a chip manufacturing company. Despite having a budget that surpassed many other organizations, he acknowledged that his organization still faced successful cybersecurity incidents. Every MTS organization must acknowledge the inevitability of compromises. These organizations cannot solely rely on outspending or outskilling threat actors, particularly those backed by nation states. For instance, according to Chris Way, the Director of the FBI, the People’s Republic of China (PRC) boasts the largest hacking program globally, surpassing the combined efforts of all major countries and outnumbering U.S. government hackers 50 to 1 (refer to minute 20 of the Select Committee on the CCP, “The CCP Cyber Threat to the American Homeland and National Security,” dated 01/31/2024). Furthermore, a 2023 MTS-ISAC report highlighted a concerning trend where countries tend to police MTS victims of cyber-attacks and attribute blame to them, rather than holding accountable the threat actor groups responsible. A critical cybersecurity objective of any cybersecurity program is “Auditable.”
- Network segmentation is critical for MTS organizations. The US Coast Guard published a simple network architecture that highlights an approach to this segmentation.
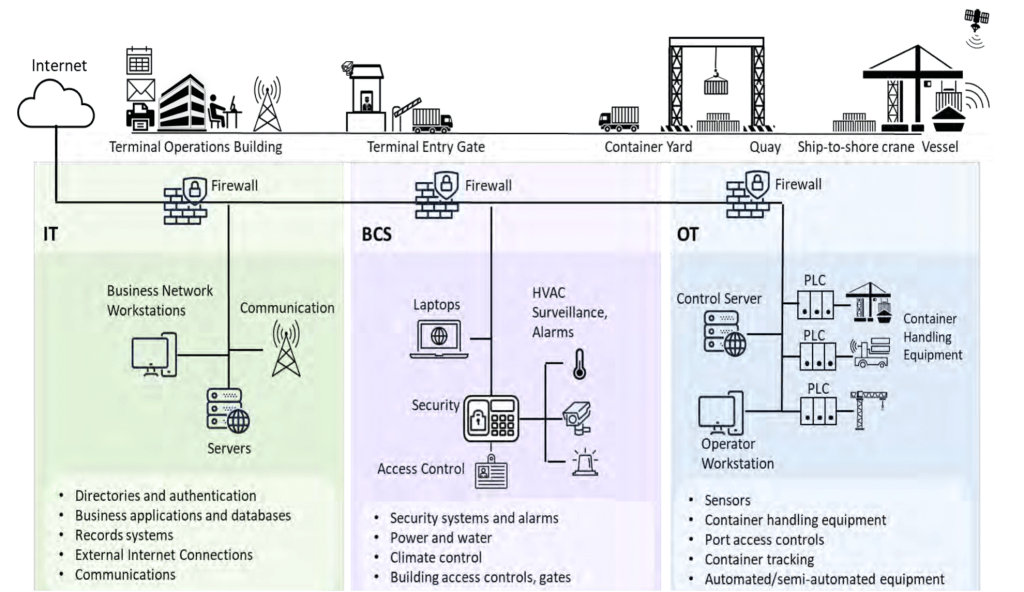
Initial Questions
- Is the business contextual architecture correct? What is missing?
- Where do requirements for Keelson come from? Below is a listing of sources for potential requirements for a company, like Keelson, operating seaport container terminals in the US. It is imperative for a company to assign a role to consistently review these sources along with others to draft company specific policies and standards and training material. Cybersecurity staff would have to collaborate with legal and compliance teams. Here is a quick list of potential sources: a) International Association of Ports and Harbors (IAPH); b) US Coast Guard (USCG). US Coast Guard has published several guidance documents: i) Navigation and Vessel Inspection Circular (NVIC 01-20) ; ii) Maritime Cybersecurity Assessment and Annex Guide (MCAAG); c) Cybersecurity and Infrastructure Security Agency (CISA); d) Baltic and International Maritime Council (BIMCO); e) International Maritime Organization (IMO).; f) Jones Walker Survey ; g) ISO/IEC 27001; h) Executive Order on Amending Regulations Relating to the Safeguarding of Vessels, Harbors, Ports, and Waterfront Facilities of the United States; h) NIST Cybersecurity Framework (version 2.0); i) Corporate CMA CMG Policies and Standards.
- Are the roles and responsibilities been clearly defined by CMA and Keelson? Why was Keelson originally setup as a wholly owned subsidiary of CMA?
