Greetings, fellow architect or cybersecurity strategist! Imagine if you had a looming deadline and a meeting scheduled with a stakeholder in just two hours, especially as a newcomer to the company or potentially a new customer, preparation is key.
In tackling this challenge, consider leveraging the Agile Security System (TASS) for a streamlined approach.
Note: for a deeper understanding of the methodology, refer to the insights provided in the Rogers post.
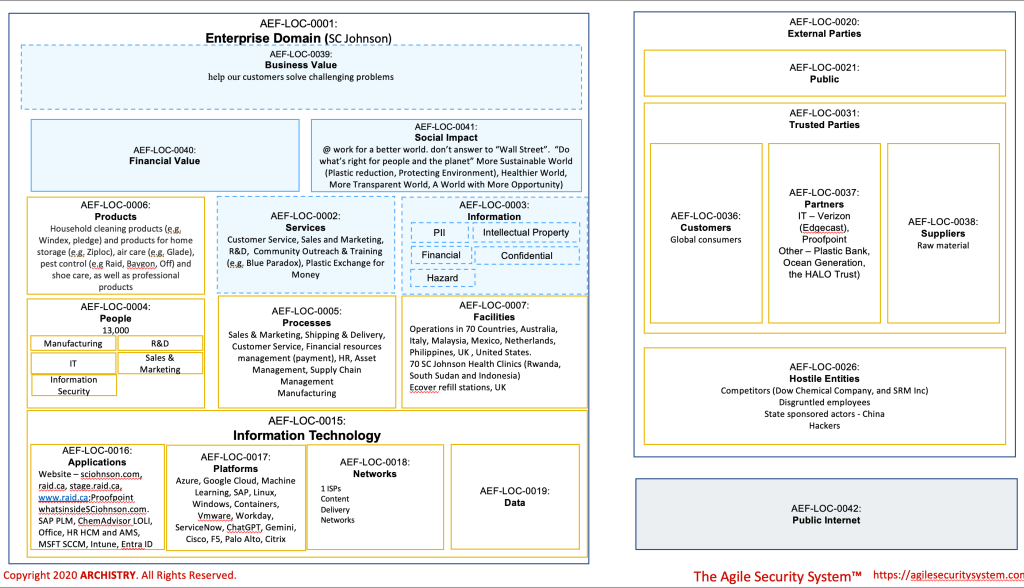
This article, however, won’t introduce new techniques; instead, it underscores the efficacy of TASS, particularly in swiftly delivering a business contextual architecture. The swiftness of TASS is attributed to key factors: simplicity over complicated models in software, a focus on iterations over perfectionism, and a commitment to re-usability.
In terms of re-usability (#3), it’s noteworthy that the domain impact worksheet incorporates elements from another manufacturing company, ON. This re-usability extends beyond the worksheet itself to encompass requirements, risks, mitigations, and even initial observations and questions specific to a particular domain. The versatility of TASS lies in its ability to adapt and apply proven elements across various aspects, facilitating a more efficient and effective approach to cybersecurity strategy. A word of caution though: do not the let beauty of this approach turn you into a “lazy” (not in smart way) and “autopilot architect.”
I prefer to “practice what I preach,” hence I’ve established a two-hour time limit to complete this post. This includes conducting research, developing the domain impact worksheet, formulating observations and questions, and finally, posting the content on the blog. And yes, I leverage ChatGPT to help improve how some of the content is written. Hopefully, ChatGPT doesn’t completely eliminate my personality from the writing!
Let me know what you think!
~R&R,
Everyone Needs Some!
Initial Observations
| Observation | Re-useable | Detailed Information |
| SC Johnson must protect their intellectual property (IP | Yes | See ON Semiconductor posting |
| SC Johnson must have advanced capabilities in intrusion detection, web security, threat intelligence, and training | Yes | See ON Semiconductor posting |
| SC Johnson security, encompassing both facility and infrastructure, including cybersecurity, is crucial for ensuring safety, operational effectiveness and profitability. | Yes | See ON Semiconductor posting |
| SC Johnson must gather and keep up with laws and regulations and translating them into physical, administrative, and technical controls | Yes | See ON Semiconductor posting Note – one unique source of requirements is the US Environmental Protection Agenda List of Lists – Consolidated List of Chemicals |
| SC Johnson must establish an Enterprise Architecture (EA) capability | Yes | See ON Semiconductor posting Note – EA function is even more important in light of SC Johnson strategy to make the world a better place through various initiatives (like Base of the Pyramid Team, Blue Paradox) |
| SC Johnson cybersecurity capabilities must encompass attack surface management and threat intelligence | Yes | See ON Semiconductor posting |
| SC Johnson must have a strategy for cloud governance, process, people and technology. | Yes | See Rogers Posting |
Initial Questions
Re-useable questions for another manufacturer organization
- Is the accuracy of the business architecture confirmed, and is there any essential component missing?
- Does a reference architecture exist for a specific plant that includes cybersecurity requirements? How is the integration handled in the event of a merger with a new company?
- What role does IT and Cybersecurity play in the expansion or installation of a new manufacturing facility?
- In what ways can Cybersecurity support and safeguard Research and Development (R&D) efforts?
- Is there a defined policy or stance regarding Generative AI, and does SC Johnson have an Emerging Technology Committee in place?
Unique Questions
- What critical applications are needed for the key processes identified?
- How integrated are SC Johnson’s partners in terms of their networks or data sharing?
- Has the executive leadership team written a “risk factors” report (like the risk factor section of a SEC filing)?
