The Why
So, you are a newly hired X at an organization. You can substitute X with CISO, architect, engineer, senior manager, consultant, sales manager etc. Maybe, you are a cybersecurity architect or enterprise architect at an existing organization and you have been tasked to develop a cybersecurity architecture strategy.
You probably have many, many questions (or you should), like…
- How do I determine what is most important to the organization?
- How do I gather and organize the various requirements from policies, standards and stakeholders?
- How do I get the “lay of the land” quickly, so I can ask people good questions and share some initial observations?
- How do you create credibility and trust?
- How do I get my organization to “shift left?”
The Approach
Over the past two years, I’ve been immersed in a transformative approach aimed at tackling these types of questions. This method, known as the “Agile Security System,” has been developed, maintained and taught by Andrew Townley (visit https://agilesecuritysystem.com for more details) and is based on SABSA. I have been a big supporter and fan of SABSA since 2018. My journey with Andrew’s methodology began during my participation in a “Building Effective Security Architectures” cohort. Subsequently, I had the opportunity to put it into practice within a healthcare organization valued at over $9 billion. To reinforce my understanding, I delved into Andrew’s book, “Getting Started with The Agile Security System,” as a refresher this year. For ongoing insights and master classes on this methodology, Andrew’s “Club” is an invaluable resource, complemented by his monthly “Security Sanity” newsletter.
Note: it’s important to clarify that my acknowledgment of Andrew Townley’s work, is not driven by any financial incentives or benefits from him. I credit him for this approach because it genuinely deserves recognition (and owns the copyrights and trade mark too).
A critical and must deliverable of the business contextual architecture of the “Agile Security System” is the “Domain Impact Worksheet.” Other deliverables include:
- Listing of requirements and objectives per domain in the “Domain Impact Worksheet.”
- Listing of risks to the objectives and requirements
- Listing of strategies to mitigate the identified risks
- Mapped relationships and approved interactions between domains
This posting focuses on the “Domain Impact Worksheet” deliverable. In Figure 1 below, the “Domain Impact Worksheet,” the interplay of blue and gold boxes unfolds. Each of these colored boxes represents a unique “domain,” a concept rooted in the idea that a domain is “any collection of elements that share a common set of characteristics that can be deployed to deliver a common purpose” (Townley, 2023). This foundational concept, courtesy of SABSA, is a noteworthy contribution to breaking down and organizing elements of an organizational. Gold domains have elements with corresponding items in the real and physical world, while blue domains organize logical elements.
The Domain Impact worksheet serves as a consistent, visual framework and communication tool for organizing elements of an organization for analysis and structuring requirements (see question #2 above). Each domain adheres to a consistent set of criteria, aiding in the determination of whether an element belongs within its confines. Moreover, each domain can have distinct requirements that must be addressed or risks mitigated via security objectives (i.e. Cybersecurity Strategy). The beauty of this system lies in its ability to nest domains within each other, forming a hierarchy of super-domains and subdomains. Subdomains domains inherit requirements from their super-domain but may also have unique requirements from their peer domains.
In essence, the “Domain Impact Worksheet” becomes a canvas illustrating (see question #3 above) the connectivity between the organization’s vital value streams and the underlying components of people, products, processes, services, facilities, information, and technology (see question #1 above). It not only visually organizes these elements but also provides foundation for showing how they interact with another within the organizational landscape. It helps you “shift left” (see question #5 above) because you start with “the business” context and creates credibility (see question #4 above) by demonstrating that you understand what cybersecurity needs to protect and enable.
One key principle embedded in “The Agile Security System” is the commitment to thorough preparation (i.e., do your homework). I complete “my homework” by utilizing various tools, including:
- SEC 10-K Document review: One valuable resource is the SEC 10-K Filings, particularly the “Risk Factors” section. This document, initially introduced to me when I was enrolled in the MBA program at Grand Canyon University, offers a business-centric perspective on cybersecurity risks alongside other organizational challenges. Instead of drowning in a sea of technical jargon, it provides a holistic view, steering clear of mere lists of CVEs or the latest cyber threats.
- SSL Labs Report Review: Provides a “grade” on the SSL hygiene of a website and type of web platform (e.g. IIS, Apache) utilized by the website.
- Shodan IO Report Review: The Shodan IO report on the main website takes the investigation further, presenting web platforms, operating systems, and even country locations.
- Searching and reviewing job descriptions. Job descriptions can be surprisingly revealing. A glance at them can provide valuable information on the technical applications and platforms actively used within the organization, offering a glimpse into its technological ecosystem.
- OSINT Framework. This is not a tool per se, but a way to query free search engines, resources, and tools publicly available on the Internet. Various tools provide information on IP addresses.
- Review the latest Verizon Data Breach report. This report furnishes incident data within a particular industry, aiding in the identification of potential risks for the organization under scrutiny.
- Prompting ChatGPT 3.5. Leveraging the power of generative AI through ChatGPT 3.5 can bring another layer of understanding. This platform not only answers questions but also provides contextual information about the organization, generating risks, and information in areas that you are not well-versed in.
- Leverage Microsoft PowerPoint, Word, Google Slides or Docs. Don’t overlook the simplicity and adaptability of familiar tools. The Microsoft PowerPoint slide, as exemplified in Figure 1, the “Domain Impact Worksheet” is based on a template from “Building Effective Security Architectures” cohort. It serves as a template for creating reusable business contextual architectures, offering a straightforward yet effective means of documentation. I also use Microsoft Word to collect and organize my notes and output from the various tools mentioned above. My notes are organized around the various domains and risk factors.
A Case Study – Rogers Corporation (Engineering and Manufacturing, ROG – NYSE)
Rogers Corporation designs, develops, manufactures and sells high-performance and high-reliability engineered materials and components to meet our customers’ demanding challenges. Rogers operates two strategic operating segments: Advanced Electronics Solutions (AES) and Elastomeric Material lSolutions (EMS).
Note – Elastomeric materials are polymers with elastic properties, capable of returning to their original shape after deformation
The “Domain Impact Worksheet” in Figure 1 summarizes part of the business contextual architecture of Rogers Corporation.
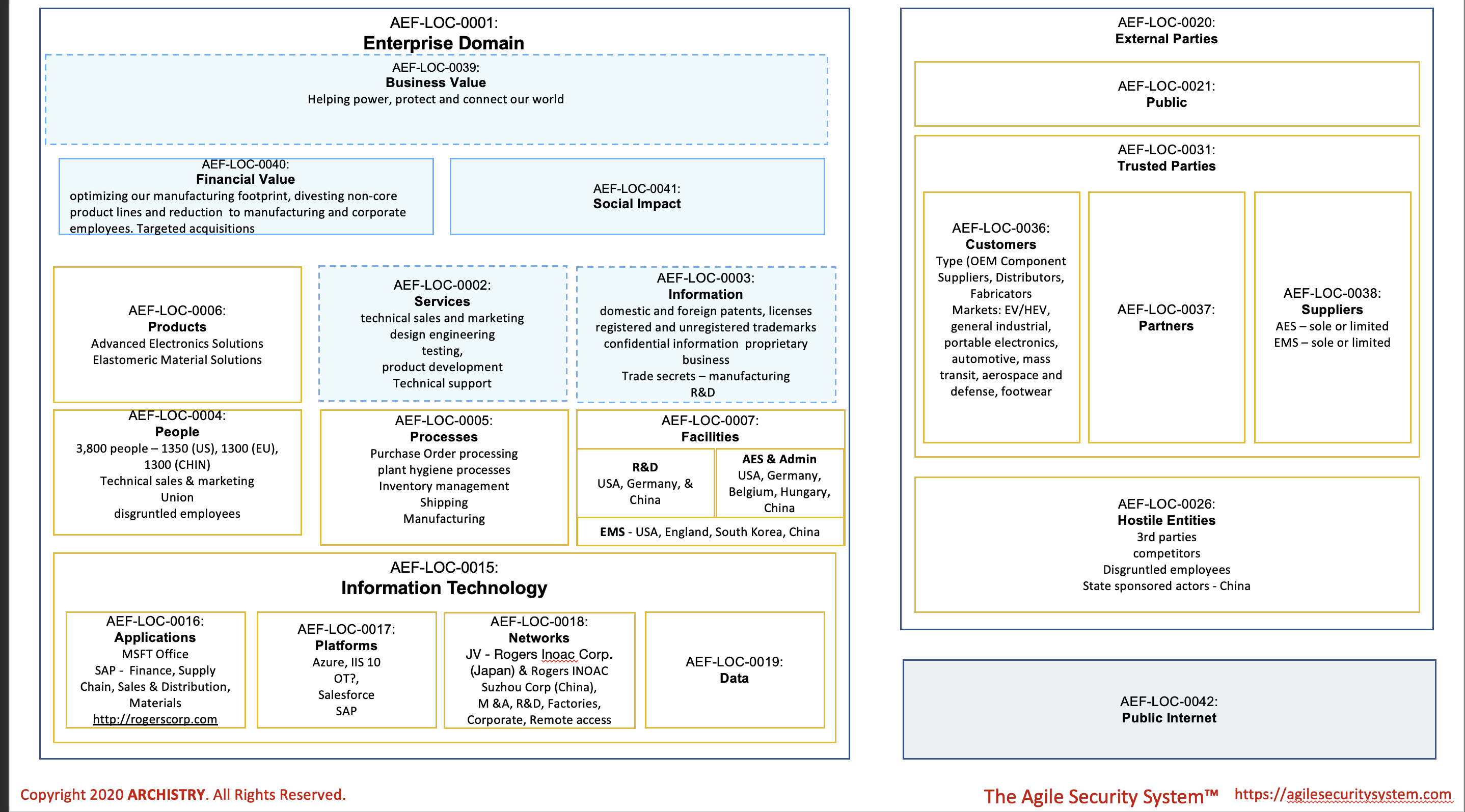
Figure 1 – Domain Impact Worksheet for Rogers Corporation
Let’s go back to question # 3 above except let’s slightly re-word it.
What are some questions and initial observations about Rogers Corporation?
Initial Observations
- Ensuring the safeguarding and facilitation of critical functions such as manufacturing, engineering, sales, financial systems, shipping, and engineering services is of paramount importance. The uninterrupted operation of factories and the timely issuance of invoices are directly tied to the financial health of the company. This principle extends to our Supply Chain partners as well. Any cybersecurity incident or unforeseen disruption stemming from poorly executed upgrades or changes has the potential to significantly impede these essential services. A comprehensive cybersecurity strategy must integrate security goals that encompass availability, change management, configuration management, monitoring, recoverability, risk management, vulnerability management, threat monitoring, threat management, and usability.(see Townley, 2023 Appendix E for definitions of these objectives or attributes).
- Securing Rogers’ proprietary information, including trade secrets such as manufacturing processes, patents, licenses, and confidential customer data, demands a strategic focus within any robust cybersecurity framework. Effectively safeguarding these critical assets necessitates the integration of security objectives that prioritize confidentiality, classification, access control, duty segregation, awareness, governance, and ongoing monitoring (see Townley, 2023 Appendix E for definitions of these objectives or attributes).
- The business requirements for writing cybersecurity policies and ensuring Rogers complies with various regulations come from several sources. These requirements must be harmonized and ideally aligned with a centralized control framework, such as the Unified Compliance Framework. To achieve this, an evaluation of the following regulations for relevance is essential: a) EU General Data Protection Regulation; b) Cybersecurity Law of the People’s Republic of China (2017); c) National Security Law (2015, China); d) Act CXII of 2011 on Informational Self-Determination and Freedom of Information (Privacy Act, Hungary); e) Personal Information Protection Act (PIPA, South Korea); f) California Consumer Privacy Act; g) Sarbanes-Oxley Act (US); h) Securities and Exchange Commission (SEC) Guidance, including the new incident disclosure; i) State Data Breach Notification Laws. Consequently, the cybersecurity strategy must be structured to address the security objectives of auditability, legality, and compliance (see Townley, 2023 Appendix E for definitions of these objectives or attributes).
- Rogers appears to have a presence in Azure. Any identified security objectives and cybersecurity strategy needs be extended to this environment. In fact, Rogers’ IT Cloud strategy should have a cybersecurity section that addresses these objectives along with cover other areas: a) multi-disciplinary risk framework to manage risks in the cloud; b) a control framework that is cloud service provider agnostic, but mapped to Azure services; c) approach on how zero trust will be implemented; d) the identity and access management approach; e) the use of a cloud-native application protection platform (see https://www.gartner.com/reviews/market/cloud-native-application-protection-platforms for definition); f) cybersecurity operations center capabilities (see https://www.mitre.org/sites/default/files/2022-04/11-strategies-of-a-world-class-cybersecurity-operations-center.pdf for a great resource on SOCs).
Initial Questions
- Is the accuracy of the Domain Impact worksheet assured, or are there crucial elements missing?
- How do members of the engineering and sales force teams obtain access to the essential data required to support customers effectively?
- What components of the CIS Critical Security Controls are in place for the Information Technology parent domain in terms of people, process and technology?
- Who is accountable and responsible for collecting and maintaining cybersecurity and privacy requirements from the various countries that Rogers operates in?
- How does the organization navigate the complex situation of operating a factory in China while acknowledging documented evidence indicating that China or affiliated actors engage in active intellectual property theft, as highlighted in instances such as those presented in the document at https://foreignaffairs.house.gov/wp-content/uploads/2020/02/Egregious-Cases-of-Chinese-Theft-of-American-Intellectual-Property.pdf?
- In what manner is the network segmented to heighten detection capabilities and restrict the potential impact area in the event of a compromise?
- What categories of Operational Technology (OT) are currently in operation within the environment, and does OT pose a significant risk for Rogers? For a comprehensive definition of OT, refer to https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-82r3.pdf. The latest Verizon Data Breach report indicates that incidents involving OT remain relatively small, particularly in the manufacturing industry, it remains prudent to stay vigilant given the potential impact, as recommended by Verizon.
- What is the cloud governance for the Azure environment? Does it follow the recommended Microsoft governance model, including the team structure? Has the environment been architected to align with the Microsoft Cloud Adoption Framework, especially the use of landing zones?
That is it. Let me know your thoughts. Happy Holidays..
~R&R
Dashing through the snow
In a one-horse open sleigh
O’er the fields we go
Laughing all the way
Bells on bobtails ring
Making spirits bright
What fun it is to create & share
architectures tonight.
